Reset Windows Password:
dump domain cached passwords
Selecting data source
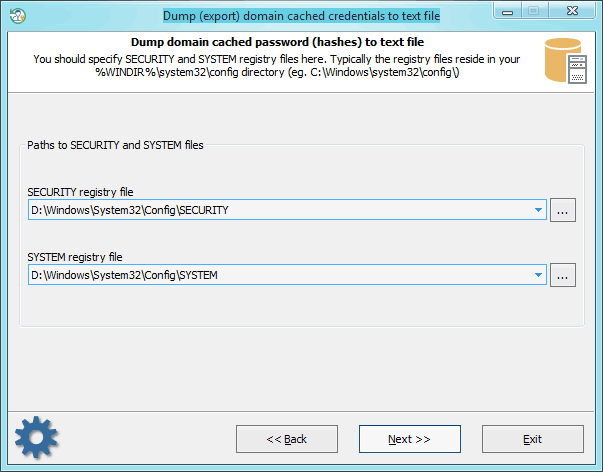
For decrypting domain cached credentials, the program needs to 'know' the location of two system registry files: SECURITY and SYSTEM. Select them from the list or, if the application was unable to locate them, provide the path to them manually.
Dump domain cached credentials
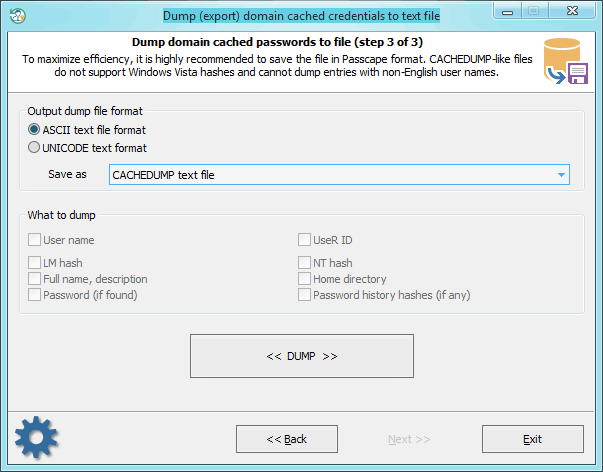
The final dialog provides just two options:
-
Dump file format. ASCII is good for all cases, but problems may occur with non-English usernames and, respectively, with further analysis and decryption of those hashes. UNICODE supports all languages, but compatibility problems may occur when reading this format in different applications.
-
Dump file type can be either CACHEDUMP - a simple but widespread format. No compatibility problems will occur. However, this format imposes a number of restrictions. First, it does not support non-English user names. Respectively, further on, you will be unable to decrypt the account password, as it is bound to the name. Second, the current version of the CACHEDUMP format does not support operating systems Windows Vista and higher.
Passcape format - free from these disadvantages and can be successfully used in password audit and recovery applications like, for example, Network Password Recovery.