Windows Password Recovery - Windows Credentials Explorer
The Windows Credential Manager is a built-in feature in Windows 7 and later operating systems designed to provide a secure storage facility for personal data and user credentials. It acts as a central repository, allowing users to manage a variety of credentials like usernames, passwords, certificates, and generic credentials with ease and convenience. The Data Protection Application Programming Interface (DPAPI) ensures that these credentials are safely protected.
The Credential Manager comes with an interface that enables authorized users and applications to manipulate and access stored credentials. In the latest versions of Windows, the Credential Manager supports syncing credentials across devices via a Microsoft account. This makes it more convenient for users to gain access to resources across different systems.
Using the Credential Manager APIs (CredUI or CredProv), applications can retrieve or delete previously saved credentials, create new ones, or use stored credentials to authenticate without having to prompt the user repeatedly. It's worth noting that these APIs work solely for the logged-on user account on the current system.
The Windows Credentials Explorer tool allows you to decrypt credentials stored in the Windows Credential Manager by directly accessing raw data, without relying on any known Credential Manager APIs. This means that you can retrieve credentials from any user account on any system.
1 Setting the Source of Credentials
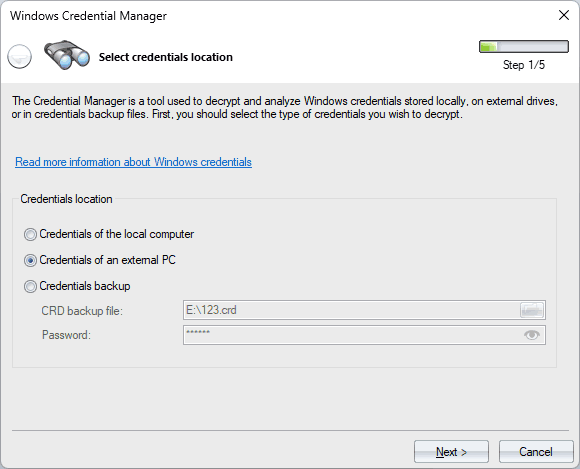
The first dialog window prompts you to select the source of the credentials you wish to decrypt. You have three options to choose from:
- Local PC: Select this option to decrypt credentials stored on your current machine.
- External PC: Choose this option to decrypt credentials stored on an external hard drive.
- Backup File: If you have a backup file containing the credentials you wish to decrypt, select this option. Credentials backup files usually have a *.crd extension and securely store encrypted copies of all credentials in one place. If you know the password the .crd file was protected with, you can unprotect and view stored credentials using this option of the Windows Password Recovery.
2 Specifying the Windows and User Profiles Folders
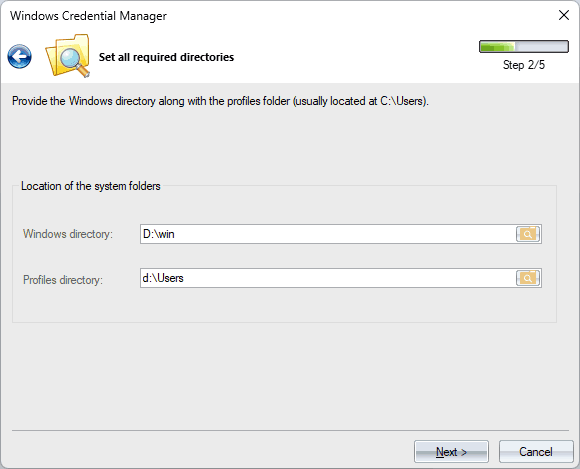
In the second dialog, you must provide the location of the Windows directory and the user's profiles folder. This information is crucial for the program to locate the appropriate files and folders related to the Credential Manager.
3 Selecting User Account
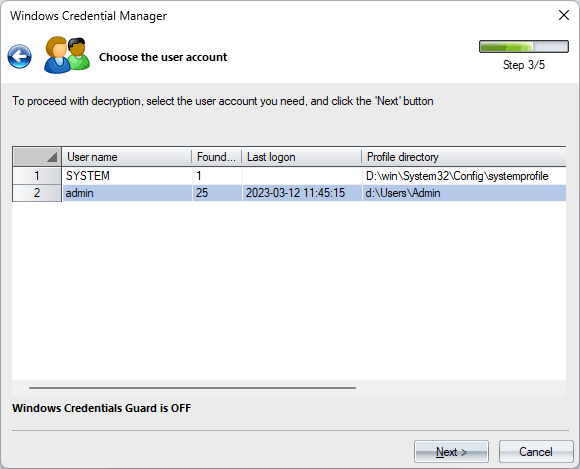
The third dialog of the Wizard scans for user accounts based on the specified folders and displays a list of user names found. From this list, choose the user account you want to search and decrypt credentials for.
4 Entering User Password or PIN
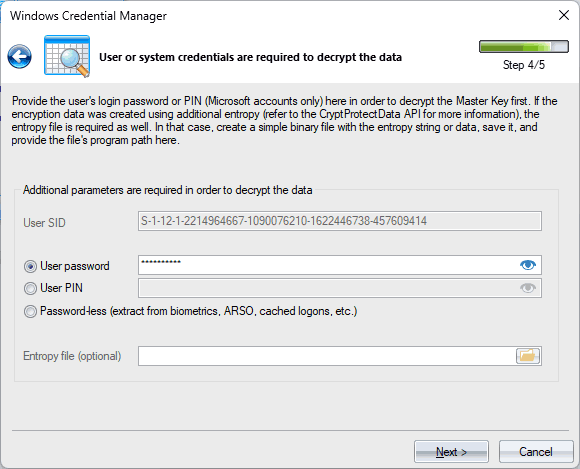
Once you select the user account, provide either the password or PIN (Microsoft account only) associated with that account. This information is necessary for decrypting credentials that are protected with DPAPI. Please ensure that you have the authentication details correct before proceeding. The password-less decryption is the state-of-the-art feature worth trying out if the user password is forgotten or unknown for some reason. If the program locates any sensitive information like biometrics, ARSO, cached logon, etc., you can decrypt credentials without providing the user password or PIN.
5 Locating and Decrypting Windows Credentials
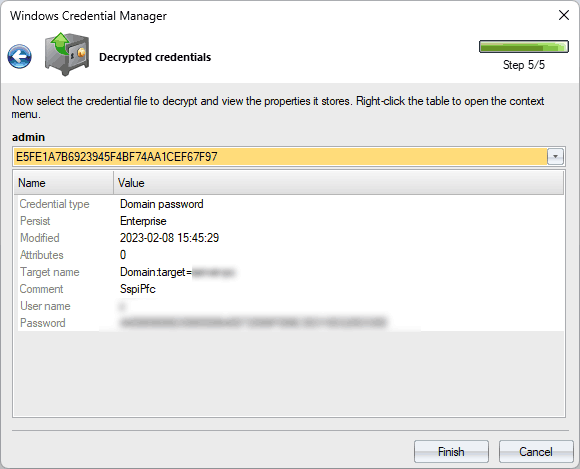
In the final dialog box, the program searches for any stored credentials associated with the selected user account and decrypts them using the provided authentication details. Once the decryption process is complete, you can view properties of each decrypted credential, such as network or user name, password, and other relevant information.





