Reset Windows Password v14.2
Telegram data recovery, Photo Database and Media Player investigation tools, and some more
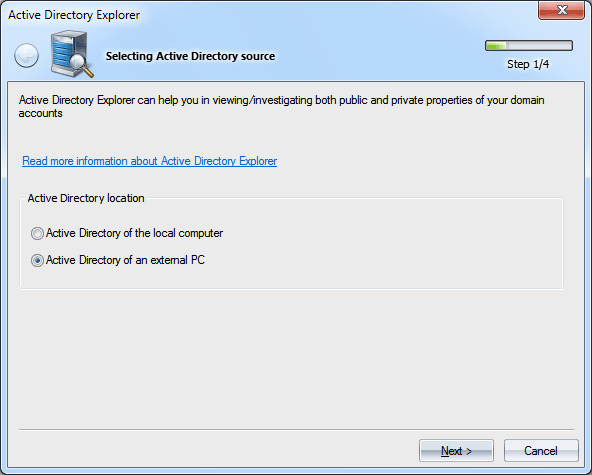
Windows Password Recovery - Active Directory Explorer
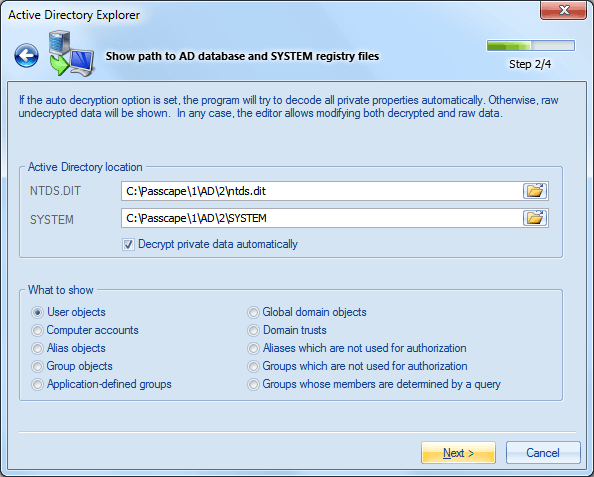
For safety reasons, the editor mode is available for external databases only!
You should also specify what object you want to display. There are 10 types of domain objects. See the table below.
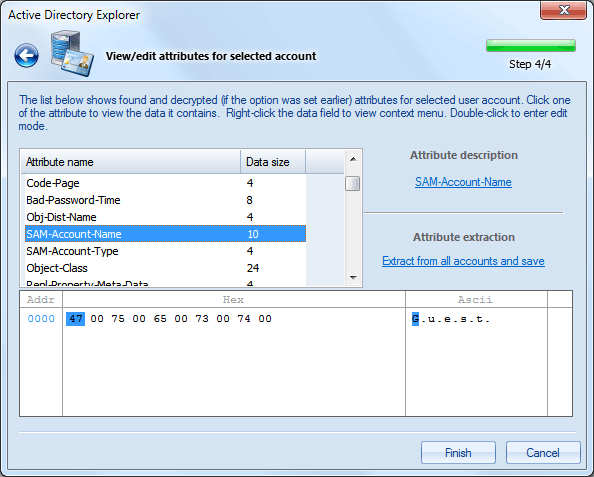
Common-Name
The name of the account. DBCS-Pwd
Contains LAN Manager password of the account. Unicode-Pwd
The password of the user in Windows NT one-way format (OWF). Note that you cannot derive the clear password back from the OWF form of the password. Lm-Pwd-History
Contains the password history of the user in LAN Manager one-way function format. The attribute is used for compatibility with LAN Manager 2.x clients, Windows 95, and Windows 98. Nt-Pwd-History
The password history of the user in Windows NT OWF format. Primary-Group-ID
Relative identifier (RID) of the primary group of the user. This is Domain Users group, by default. Bad-Pwd-Count
Contains the number of times the user tried to log on to the account using an incorrect password. Admin-Count
Indicates that the account is a member of one of the Administrative groups (directly or transitively). Logon-Hours
The hours that the user is allowed to logon to the domain. Last-Logon
The last time the user logged on to the account. Bad-Password-Time
The last time the user attempted to log on to the account with an invalid password. This value is stored as a large 8-byte integer that represents the number of 100 nanosecond intervals since January 1, 1601 (UTC). Last-Logon-Timestamp
This is the time that the user last logged into the domain. Pwd-Last-Set
The date when the password for this account was last changed. Account-Expires
The date when the account expires. A value of 0 or 0x7FFFFFFFFFFFFFFF indicates that the account never expires. Supplemental-Credentials
Stores the encrypted version of the user's password. Used in authentication. User-Account-Control
Flags that control the behavior of the user account. This value can be a combination of one or more of the following values. 0x00000001 Logon script is executed for the account. 0x00000002 The account is disabled. 0x00000008 Home directory is required. 0x00000010 The account is currently locked out. 0x00000020 No password is required. 0x00000040 The user cannot change the password. 0x00000080 The cleartext password is to be persisted 0x00000100 This is an account for users whose primary account is in another domain. 0x00000200 This is a default account type that represents a typical user. 0x00000800 Trust account for a system domain that trusts other domains. 0x00001000 This is a computer account for a computer that is a member of this domain. 0x00002000 This is a computer account for a system backup domain controller that is a member of this domain. 0x00010000 The password for this account will never expire. 0x00020000 This is an MNS logon account. 0x00040000 The user must log on using a smart card. 0x00080000 The account, under which a service runs, is trusted for Kerberos delegation. 0x00100000 The security context of the user will not be delegated to a service even if the service account is set as trusted for Kerberos delegation. 0x00200000 Restrict this principal to use only Data Encryption Standard (DES) encryption types for keys. 0x00400000 This account does not require Kerberos pre-authentication for logon. 0x00800000 The user password has expired. 0x01000000 The account is enabled for delegation. Enables a service running under the account to assume a client identity and authenticate as that user to other remote servers on the network. 0x04000000 The object is a read-only domain controller (RODC) | |||||||||||||||||||||||