Dictionary attack
In contrast with a brute-force attack, where all possibilities are searched through exhaustively, a dictionary attack only tries possibilities which are most likely to succeed, typically derived from a wordlist or a dictionary. Generally, dictionary attacks succeed because many people have a tendency to choose passwords which are short, single words in a dictionary, or are simple variations that are easy to predict.
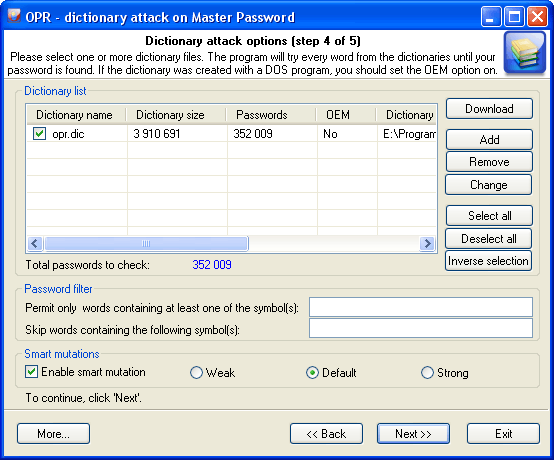
All dictionary attack options are conditionally split into three groups:
Dictionary list
In the first group of options, you must set at least one dictionary for the attack. If the dictionary was created with a DOS program, the option 'Dictionary file in DOS encoding' must be selected when adding this dictionary to the list. The program comes with a short English wordlist. For the complete list of dictionaries, check out our wordlist collection, please. Or you can use our online dictionaries as an alternative.
Password filter
To crop unnecessary passwords, you can use two simple filters. If you have set at least one character in the first 'Include' filter, all passwords that do not contain that character will be ignored (skipped) by the program. The second 'Exclude' filter is totally opposite.
Password mutations
The last group of options manages mutations for each password to be verified. You can set up to three mutation rules: Weak - less number of mutations and, in its turn, greater verification speed; Strong - for the greater number of mutations, to the prejudice of the speed, and the happy medium, Default option.
Dictionary attack fits perfectly for short and common passwords. To recover long passwords consisting of several words, consider using a phrase attack or combined dictionary attack.

