Windows Password Recovery - DPAPI Master Key analysis
A master Key is 64 bytes of data, that are used as the primary key when decrypting a DPAPI blob. A user's Master Key is encrypted using the user's logon password.
Set path to the Master Key file and specify the user SID
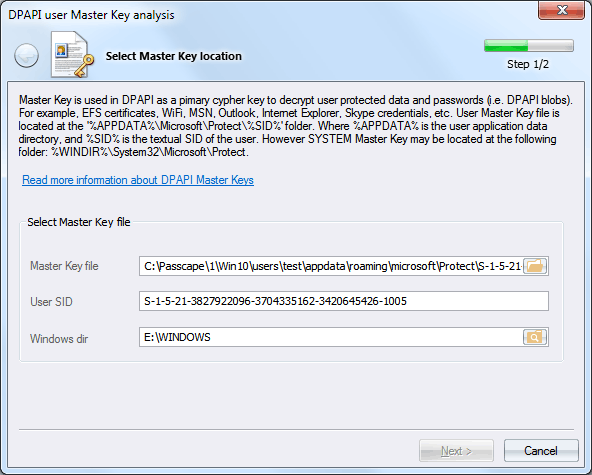
All of that user's Master Keys are located in %APPDATA%\Microsoft\Protect\%SID%. For example,
C: \Users\ John\ AppData\ Roaming\ Microsoft\ Protect\ S-1-5-21-2897849034-3956381361-16091305341-1001\ 23ab9bc1-9397-4cb1-ab74-7166ed6a8713
The system's Master Keys are stored in %SYSTEMDIR%\Microsoft\Protect folder.
Analyzing Master Key
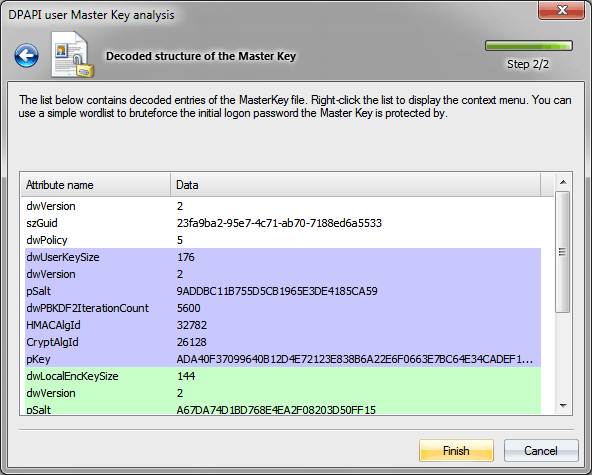
A Master Key file is a binary structure, which consists of a service header and four slots, namely:
the actual user's Master Key, the local encryption key (for unprotecting local backup key), local backup key (in Windows 2000) or CREDHIST GUID (in Windows XP and higher) and the domain backup key.
The Master Key structure list consists of attribute names (i.e. binary fields) and values that correspond with them. Each section is uniquely colored:
- field with header attributes
- slot with user's Master Key attributes
- slot with Local Encryption Key attributes
- slot with Local Backup Key or CREDHIST file's GUID attribute
- slot with Domain Backup Key attributes
Now, a little more detail.
Header attributes
dwVersion - Master Key file version.
szGuid - Master Key textual GUID. It normally matches the file name.
dwPolicy - various flags. For example, if bit 3 is set, the program uses the SHA1 password hash when decrypting a user's password; otherwise, it uses MD4. Thus, in Windows 2000 this bit is always cleared. A set bit 2 tells us that backup is required for the Master Key.
User's Master Key attributes
dwUserKeySize - current slot length.
dwVersion - data structure version. Version 1 implements only attribute with salt.
pSalt - pSalt - salt, i.e. 16 random bytes of data, involved in the decryption of the Master Key and preventing data attacks using rainbow tables.
dwPBKDF2IterationCount - iterations in the PBKDF2 encryption key generation function.
HMACAlgId - hashing algorithm identifier.
CryptAlgId - encryption algorithm used.
pKey - user's encrypted Master Key.
Local Encryption Key attributes
dwLocalEncKeySize - current slot length.
dwVersion - data structure version. Win2K uses only one attribute with salt.
pSalt - salt.
dwPBKDF2IterationCount - iterations in the PBKDF2 encryption key generation function.
HMACAlgId - hashing algorithm identifier.
CryptAlgId - encryption algorithm used.
pKey - encrypted Local Encryption Key, used for decrypting Local Backup Key in Windows 2000.
Local Backup Key attributes (Windows 2000)
dwLocalKeySize - current slot length.
dwVersion - data structure version.
pSalt - salt.
pKey - encrypted Local Backup Key.
CREDHIST file's GUID attributes (Windows XP and higher)
dwLocalKeySize - current slot length.
dwVersion - data structure version.
guidCredHist - CREDHIST file binary identifier.
Domain Backup Key attributes
dwDomainKeySize - current slot length.
dwVersion - data structure version.
pSalt - 16 random bytes of data, involved in the decryption of the Master Key and preventing data hacks using rainbow tables.
dwPBKDF2IterationCount - iterations in the PBKDF2 encryption key generation function.
HMACAlgId - hashing algorithm identifier.
CryptAlgId - encryption algorithm used.
pKey - encrypted Domain Backup Key. Its decryption requires the domain controller RSA private key, stored in Active Directory database.
To decrypt a Master Key, you must know the owner logon password. From the context menu, you can check the password for that Master Key and even try to guess one using a dictionary. However, don't flatter yourself too much. While in Windows 2000 the search speed is ranged in tens and even hundreds of thousand passwords per second, in Windows 7 the count goes by single items. See the table below (the speed is measured on a single-core Intel Q8400 CPU).
| Operating System |
Encryption algorithm |
Hash function |
PKCS#5 PBKDF2 rounds |
Password check speed (p/s) |
| Windows 2000 |
RC4 |
SHA1 |
1 |
95000 |
| Windows XP |
3DES |
SHA1 |
4000 |
76 |
| Windows Vista |
3DES |
SHA1 |
24000 |
12 |
| Windows 7 |
AES256 |
SHA512 |
5600 |
10 |
| Windows 10-11 |
AES256 |
SHA512 |
8000 |
7 |


