Wireless Password Recovery - loading WPA hashes from network dump files
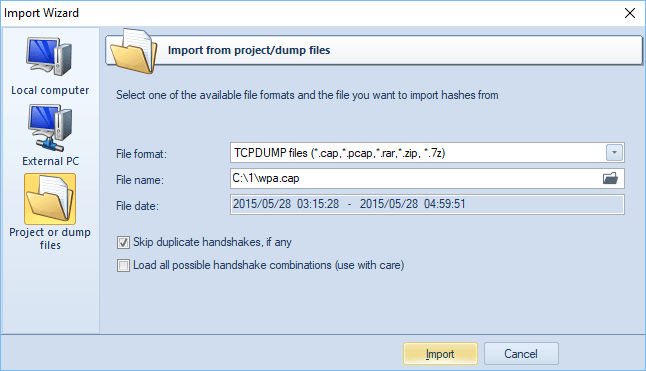
Finally, you can load WPA-PSK hashes to project by importing them from other applications or from network traffic dumps. The following formats are supported:
- TCPDUMP (*.cap, *.pcap, *.tcpdump, *.txt, *.rar, *.zip) - de-facto standard among packet sniffers, designed for intercepting, parsing, and storing TCP IP and other packets sent over the network. The following popular solutions can export network packets to TCPDUMP file: airodump-ng, CommView for Wi-Fi, OmniPeek, Sniffer Global, Wireless Snif, Wireshark, etc. Network packets to be loaded must contain authentication data (authentication handshake) between access point and client. RAR and ZIP-packed dumps are supported as well.
- Tamosoft CommView dump file (*.ncf) - this file format is used by CommView for Wi-Fi.
- WPA-PSK PMK hash files by InsidePro (*.txt). This format is similar to a PWDUMP-like text file and is used in InsidePro. It may have problems with some SSID names.
- Elcomsoft EWSA project files (*.wkp). This format is used by Elcomsoft Wireless Security Auditor.
- WPA-PSK hashes in the HashCat (*.hccap, *.hccapx, *.hc22000) formats are used in Hashcat.
- WPA-PSK textual dumps in John the Ripper format.
- WIFIPR export files (*.wifiprdump). This text container is a native format of the Wireless Password Recovery and is used for exporting and importing WPA-PSK hashes. Properly handles non-standard SSID names.
- Textual files with PMKID - files in hashcat format that holds PMKID entries.
TCPDUMP and CommView dumps have also support for PMKID in addition to regular handshakes.
Additionally, the program has a couple of options (available for some formats only) for more accurate load:
- Skip duplicate handshakes, if any. If set, the option guarantees to load only unique handshakes in the file scope. Duplicate items will be ignored. It is recommended for this option to be set on always.
- Load all possible handshake combinations. Sometimes it is very difficult to extract valid handshakes out of a capture file, especially when the WPA-PSK 4-way handshake is suppressed by and massively alternate with deauthentication packets or when the source file is broken. Unfortunately, there's no way to determine whether a handshake is valid or not. When this option is set, the program guaranteed extracts at least one valid handshake, if one exists. The backside of this option is that hundreds or even thousands of trash handshakes might be generated along with valid items. Thus, it is highly recommended to use it in conjunction with multimode (simultaneous recovery of all handshakes with the same SSID) only.
Upon importing hashes, the program automatically launches the
Preliminary recovery on the first valid hash. This action is optional and can be disabled in general settings. The default state is enabled.

