Wireless Password Recovery - brute-force recovery
To put it in simple words, brute-force recovery guesses a password by trying all probable variants by given character set. Eg. checking all combination in lower Latin character set, that is 'abcdefghijklmnopqrstuvwxyz'. Brute-force recovery is very slow. For example, once you set lower Latin charset for your brute-force attack, you'll have to look through 208 827 064 576 variants for 8 symbol password. It is rarely used for now because WPA password recovery speed is extremely low compared to other algorithms.
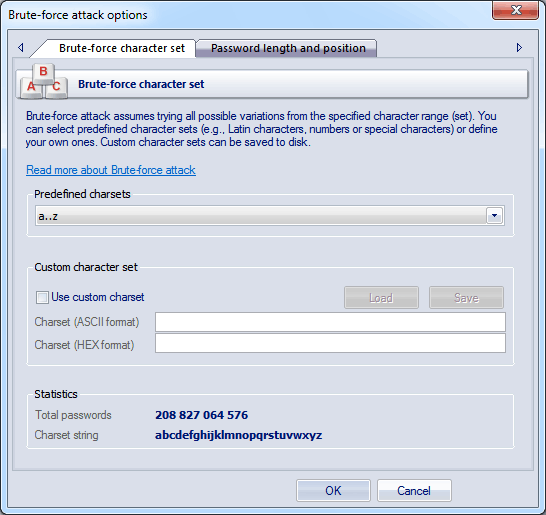
The brute-force attack options consist of two tabs.
The first tab is for setting the range of characters to be searched. You can use the predefined sets or create your own ones. To define your own character set, activate 'Custom charset'. This will enable two fields for defining a custom character set: the first one - for entering ASCII characters, the second one - for entering non-printable characters. The program comes with several custom-defined character sets.
On the second tab, set the minimum and maximum length of the passwords to be searched. Set a starting password is allowed as well.
Don't forget about 8-character limit in WPA-PSK password specification!

