Windows Password Recovery - Passcape table attack
Passcape Rainbow Tables are the next logical development of simple pre-calculated tables. They are most suitable for the recovery of meaningful combinations and complex passwords of literally unlimited length.
The original method of simple rainbow tables
The operating principle of simple rainbow tables consists of setting a character range (for example, a..z) and maximum password length, followed by the calculation of all the possible variants and the generation of millions of chains. Each chain is calculated by the formula:
P0 -> hash(P0) -> H1 -> R(H1) ->
P1 -> hash(P1) -> H2 -> R(H2) ->
P2 ...
where P – password, hash – hashing function, R – reduction function. Thus, from the original password, the hashing function produces a hash, which the reduction function then converts into the next password, and the process repeats all over again and generates chains. Each chain stores only the original and final value. Storing only the first and the last hash is an operation leading to compromise and saving memory at the cost of time spent on cryptanalysis.
To recover a sought password, it undergoes hashing and the reduction function and then is looked up in the table. For that purpose, a keychain is generated beginning with R(Hn) up until the maximum chain length. If Hn is obtained with the password used when creating the table, we finally get the key that matches the key of the respective chain. This last key was saved in the table along with the first key of the chain. Using the first key of the chain, we can recover the entire chain, in particular, the value right before R(Hn). That is actually the key that was used for generating Hn, our sought password.
Operating principle of Passcape rainbow tables
Recovery using Passcape rainbow tables is pretty much the same as recovery using simple rainbow tables. However, unlike the latter, it is sort of a hybrid of Fingerprint and simple table attacks, where instead of setting a specific character range passwords are validated within a so-called 'word footprint' range. The idea of the Fingerprint attack developed at Passcape comes down to taking the source dictionary and creating a bank of word footprints (fingerprints), necessary for validating the password, out of that dictionary; then, during the attack, we search for all possible variants of words that consist of two such footprints.
Similar to the Fingerprint attack, Passcape rainbow tables first create a bank of footprints for words from a user’s wordlist. The word footprint bank is an analog to the character set in simple rainbow tables. It is used for both creating Passcape tables and validating passwords. Thus, a Passcape rainbow table consists of one or more *.prt files (the actual tables) and a bank оf word footprints (*.prti), which can be engaged only with tables that were created with it.
There are a number of advantages in using word footprints instead of character sets when creating tables:
- The length of passwords validated with Passcape tables is literally unlimited. Unlike with simple rainbow tables, which practically cannot be created for passwords longer than 9 characters, with Passcape tables one can recover both one-character and 50-character password with the same probability.
- The character set in the regular table greatly affects its critical parameters: the wider the character range, the greater the chain length or the total number of chains for storing success rate (percentage of success in finding password) of the table must be. In a Passcape table, a character set does not affect the critical parameters of the table.
- Plain tables have certain difficulties when generating tables for validating passwords in national character sets; not all programs properly handle such tables, and not all can create them. With Passcape rainbow tables, when generating tables, for example, for Russian passwords, one can simply specify the source dictionary in Russian.
- With Passcape tables, passwords are searched for using more meaningful combinations; however, that largely depends on the source dictionary.
These can be referred to as drawbacks of Passcape rainbow tables:
- Not all source dictionaries are equally suitable for the tables. Using large dictionaries (normally greater than 1 MB) generates too large of a footprint bank; respectively, creating tables may require significant time and resources.
- Using dictionaries with long words or phrases is discouraged due to the above-mentioned reason.
- Rainbow table attack consumes a lot of resources: the footprint bank must fully fit the computer’s RAM.
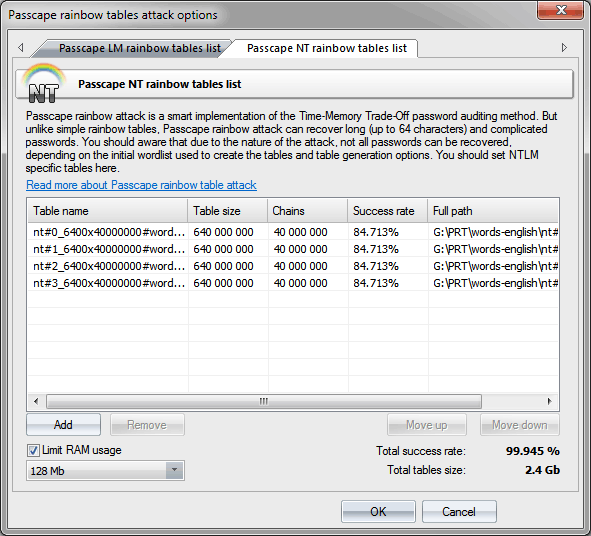
Passcape rainbow table attack settings
Passcape rainbow table attack settings are rather trivial. Specify one or several *.prt tables, which should reside in the same directory as the footprint bank (*.prti file). Since this attack consumes more RAM than the attack that uses simple rainbow tables, it is recommended to limit the amount of RAM that can be consumed by adjusting the respective option.
To create your own tables, you can take advantage of the respective tool.
You can download sample Passcape tables for this attack from our website.
Tables can crack only the hash function they were created for, i.e. NT tables can crack only NT hash!

