Windows Password Recovery - GPU mask attack
Mask options
GPU mask attack is an irreplaceable tool when you know a part of the password or have any specific details about it. For example, when you know that the password consists of 12 characters and ends with the qwerty, it is obvious that searching the entire 12-character range of passwords is unreasonable (and useless, for it takes ages to complete). All that would be required in this case is to guess the first 6 characters of the sought password. That is what the mask attack is for.
In our case, we could define the following mask: %c%c%c%c%c%cqwerty. That means that the program would successively check the following combinations: aaaaaaqwerty, aaaaabqwerty, aaaaacqwerty .. zzzzzzqwerty. If the original password is 'secretqwerty', it perfectly hits the range.
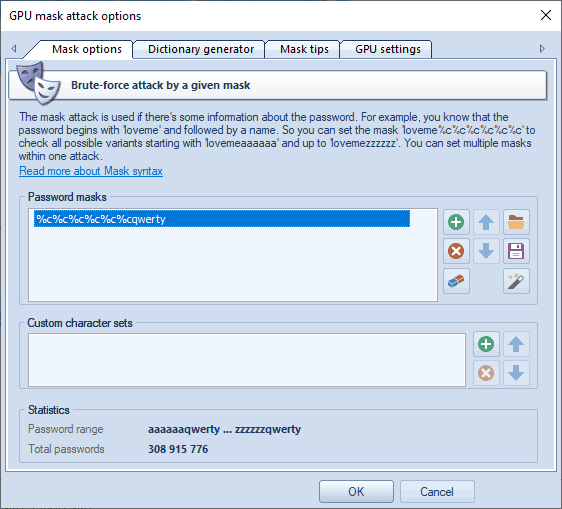
The group of the Password Masks options is aimed to set a mask (or several ones), that will be used to generated passwords by. In most cases, if you know a part of the password, it is enough to specify a single mask. When a mask is selected, the statistics group shows the range of output passwords and the number of passwords generated by this mask. You can save your masks to disk to use it in another project, for example. The program also allows you to generate dictionaries by given masks.
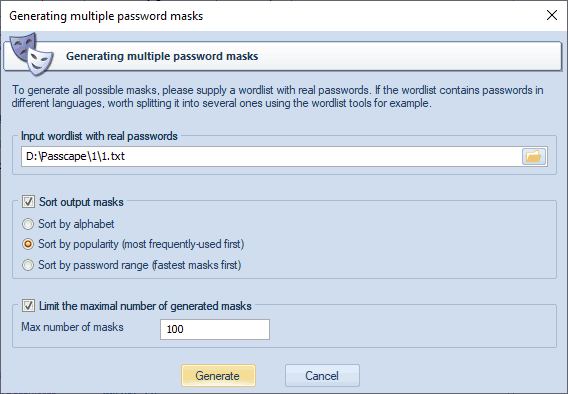
Suppose that you have a list of decrypted passwords and you would like to generate mask templates out of these passwords. Nothing easier. Run the mask generator and show the path to your password list there. You can sort the resulting masks alphabetically, popularity, or by search range (the fastest go first).
Dictionary generator
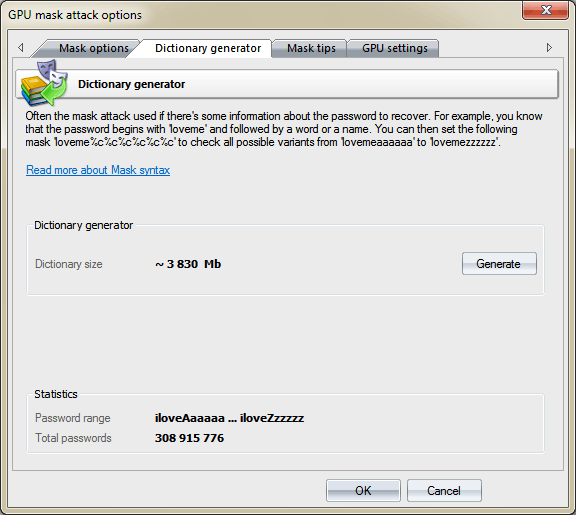
By switching to Dictionary generator tab, you can generate your own dictionary by a given mask, and save it to disk.
Mask tips
The third tab of the mask options contains a short description of the mask syntax and a couple of examples. The mask syntax is pretty simple and consists of static (unmodifiable) and dynamic (modifiable) characters. Dynamic characters always have a leading %. For example, if you set the mask secret%d%d%d%d, the program will generate 10000 passwords (secret0000, secret0001, secret0002 .. secret9999).
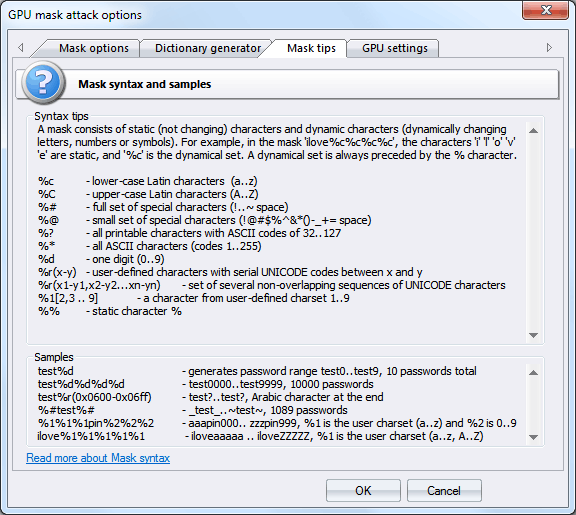
Windows Password Recovery supports the following dynamic mask sets:
| %c |
lower-case Latin characters (a..z), 26 symbols |
| %C |
upper-case Latin characters (A..Z), 26 symbols |
| %# |
full set of special characters (!..~ space), the total of 33 symbols |
| %@ |
small set of special characters (!@#$%^&*()-_+= space), 15 symbols |
| %? |
all printable characters with ASCII codes of 32..127 |
| %* |
all ASCII characters (codes 1 through 255) |
| %d |
one digit (0..9) |
| %r(x-y) |
user-defined characters with serial UNICODE codes between x and y |
| %r(x1-y1,x2-y2...xn-yn) |
set of several non-overlapping sequences of UNICODE characters. |
| %1[2,3..9] |
a character from user-defined charset 1..9 |
| %% |
standalone static character % |
Some xamples:
| test%d |
will generate password range test0..test9, 10 passwords total |
| test%d%d%d%d |
test0000..test9999, 10000 passwords |
| test%r(0x0600-0x06FF) |
256 password with Arabic character at the end |
| %#test%# |
_test_..~test~, 1089 passwords |
| %1%1%1pin%2%2%2 |
aaapin000.. zzzpin999, где %1 is user-defined charset 1 (a..z), and %2 - the second user-defined charset 0..9 |
| ilove%1%1%1%1%1 |
iloveaaaaa .. iloveZZZZZ, %1 is user charset (a..z, A..Z) |
The GPU mask attack syntax differs slightly from one used in a regular mask attack. The main difference is that in GPU-based attack you can not set numbers between x and y and can not set user-defined range of variable length, i.e. the following syntax will not work for GPU mask attack: %d(x-y) and %1[2,3..9](min-max)
GPU settings
Before you can use it in an attack, you must first select the graphics card in the General Options menu.
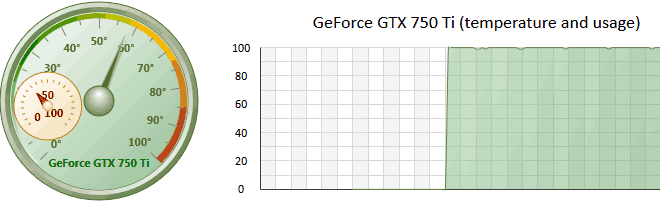
GPU configuration is pretty simple and consists of only one parameter: the number of thread blocks to run on GPU. Each block consists of either 128 or 256 threads. Thus, if you set the number of blocks, for example, 10000, the GPU will run 10000*256=2560000 threads. Each GPU thread can check multiple passwords. The total number of checked passwords greatly depends on other options. Setting the ThreadBlocks parameter smaller than 10000 on modern graphics cards, in the majority of cases, leads to poor performance. To avoid performance degradation, after setting up the parameter and running the attack, make sure the GPU load chart has close to 100% plain graphic without peeks. See the screenshot of NVidia GTX 750Ti running at 15000 blocks.