Windows Password Recovery - brute-force attack
In cryptanalysis, a brute force attack is a method of defeating a cryptographic scheme by trying a large number of possibilities; for example, exhaustively working through all possible keys in order to decrypt a message.
This definition was taken from the Wikipedia site.
Well, to put it in simple words, brute-force attack guesses a password by trying all probable variants by given character set. Eg. checking all combination in lower Latin character set, that is 'abcdefghijklmnopqrstuvwxyz'. The brute-force attack is very slow. For example, once you set lower Latin charset for your brute-force attack, you'll have to look through 217 180 147 158 variants for 1-8 symbol password. It must be used only if other attacks have failed to recover your password.
The brute-force attack options consist of two tabs.
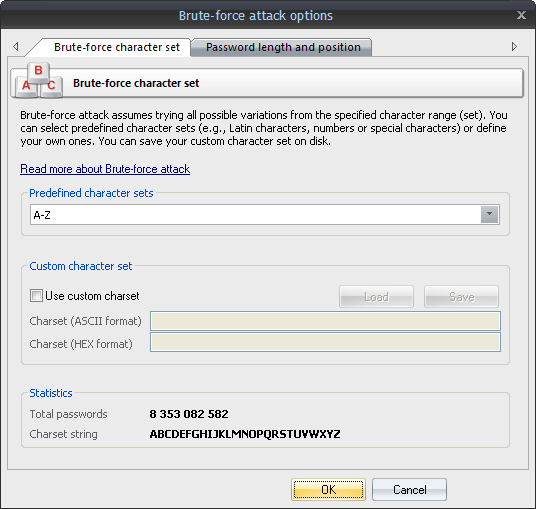
The first tab is for setting the range of characters to be searched. You can use the predefined sets or create your own ones. To define your own character set, select the option 'Custom charset'. This will enable two fields for defining a custom character set: the first one - for entering ASCII characters, the second one - for entering non-printable characters. You can save your custom character set on disk. The program comes with several examples of user-defined character sets.
On the second tab, set the minimum and maximum length of the passwords to be searched. Please note that for attacking LM hashes the maximum password length should not exceed 7 characters. You can also set a starting password, which would start the search.
Below is a table that shows password strength depending on the password length and complexity. Assuming that the recovery speed is 100M passwords per second.
| Character set |
Password length |
Password sample |
Time to crack |
| A .. Z |
5 |
CRUEL |
instantly |
| A .. Z |
6 |
SECRET |
3s |
| A .. Z |
7 |
MONSTER |
1m 23s |
| A .. Z |
8 |
COOLGIRL |
36m 11s |
| A .. Z, 0 .. 9 |
5 |
COOL3 |
instantly |
| A .. Z, 0 .. 9 |
6 |
BANG13 |
22s |
| A .. Z, 0 .. 9 |
7 |
POKER00 |
13m 26s |
| A .. Z, 0 .. 9 |
8 |
LETMEBE4 |
8h 3m 37s |
| A .. Z, a .. z, 0 .. 9 |
5 |
P0k3r |
9s |
| A .. Z, a .. z, 0 .. 9 |
6 |
S3cr31 |
9m 37s |
| A .. Z, a .. z, 0 .. 9 |
7 |
DidIt13 |
9h 56m 33s |
| A .. Z, a .. z, 0 .. 9 |
8 |
GoAway99 |
25d 16h 26m 34s |