Reset Windows Password:
dump (export) password hashes to a text file
Selecting data source
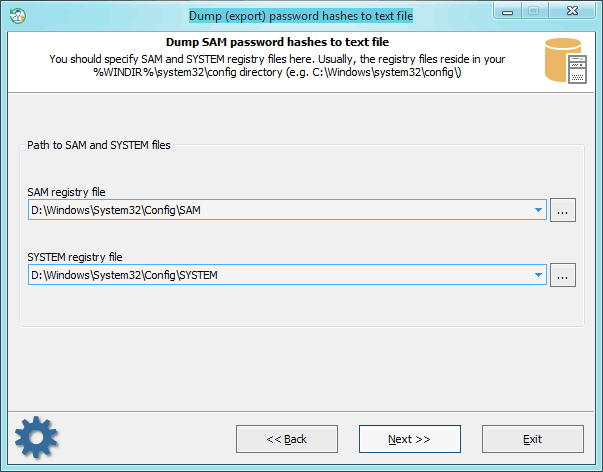
On this step, specify the location of SAM and SYSTEM files. Or, in the case with domain users, - ntds.dit and SYSTEM.
Dump password hashes
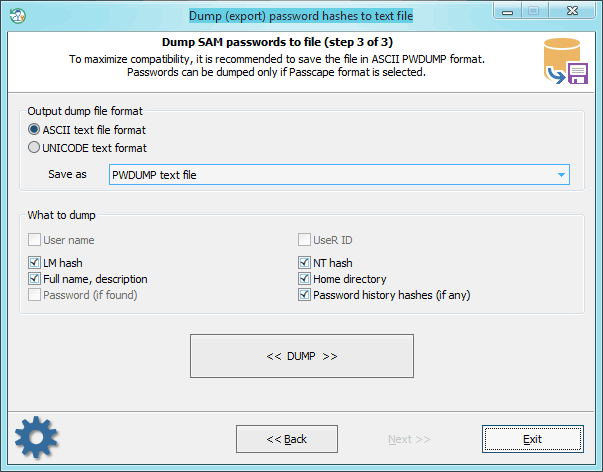
Select the format and type of the export file. While generating the dump, you can also delete, if that's no value to you, individual unnecessary attributes of the account. If the Passcape format is selected, you can also dump plaintext passwords (if ones were found). The application scans your computer for the availability of such and, if such are available, maps them to the accounts while saving to the dump file.
Plaintext passwords are stored in the domain when the option 'Store passwords using reversible encryption for all users in the domain' is set; you can find it in the group policy console.
Further on, you can use the dump file with different password audit and recovery applications.