Brute-force attack
In cryptanalysis, a brute force attack is a method of defeating a cryptographic scheme by trying a large number of possibilities; for example, exhaustively working through all possible keys in order to decrypt a message.
This definition was taken from the Wikipedia site. Well, to put it in simple words, brute-force attack guess a password by trying all probable variants by given character set. Eg. checking all combination in lower Latin character set, that is 'abcdefghijklmnopqrstuvwxyz'. The brute-force attack is very slow. For example, once you set lower Latin charset for your brute-force attack, you'll have to look through 217 180 147 158 variants for 1-8 symbol password. It must be used only if other attacks have failed to recover your password.
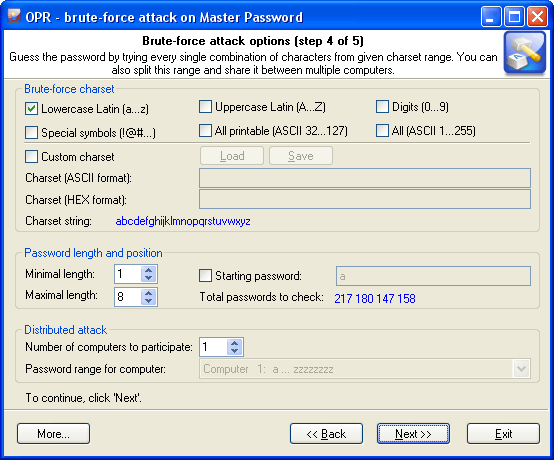
There are 3 group of options here:
Brute-force charset
Brute-force attack assumes using all possible variations from the specified character range, which is set in the first group of options. You can select and combine predefined character sets (e.g., Latin characters, numbers or special characters) or define your own ones. To define your own character set, select the option 'Custom charset'. This will enable two fields for defining a custom character set: the first one - for entering ASCII or OEM characters, the second one - for entering non-printable characters. You can save your custom character set on disk. The program comes with several examples of user-defined character sets.
Password length and position
The second group of options allows setting the minimum and maximum lengths of the password to be generated. If the last brute-force attack was interrupted or stopped, you can resume it from the last position saved by the program (see 'Starting password' option.)
Distributed attack
This group of options can be useful when you have access to several computers. In this case, the entire set of characters to be verified, if it is too large, can be split into portions and attack the password by portions on several computers at the same time. To implement that, you will need to select the number of computers participating in the distributed attack ('Number of computers to participate' option), select the same settings for all computers, and assign each computer its number in the 'Password range for computer' drop-down list.
Below is a table that shows the time required to find 6 symbol password. Assuming that the brute-force speed is 1 million passwords per second.
| Charset file name |
Charset string |
Example |
Total passwords |
Timing |
| 0-9.pcf |
0123456789 |
666929 |
1 111 110 |
1 sec |
| 1-13.pcf |
0x1 ... 0xd |
|
5 229 042 |
5 sec |
| a-z.pcf |
abcdefghijklmnopqrstuvwxyz |
qwerty |
321 272 406 |
5 min |
| a-z, 0-9.pcf |
abcdefghijklmnopqrstuvwxyz0123456789 |
asd123 |
2 238 976 116 |
37 min |
| a-z, 0-9, symbol14.pcf |
abcdefghijklmnopqrstuvwxyz0123456789!@#$%^&*()-_+= |
a#q1*9 |
15 943 877 550 |
4.5 hrs |
| a-z, A-Z.pcf |
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz |
QWErty |
20 158 268 676 |
5,5 hrs |
| a-z, A-Z, 0-9.pcf |
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz 0123456789 |
Asd123 |
57 731 386 986 |
16 hrs |
| a-z, A-Z, 0-9, symbol14.pcf |
abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ 0123456789!@#$%^&*()-_+= |
As12#$ |
195 269 260 956 |
2 days, 6 hrs |
| all.pcf |
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz 0123456789!\"#$%&'()*+,-./:;<=>?@[\\]^_`{|}~"; |
Aa1@|} |
742 912 017 120 |
8 days, 15 hrs |

