Artificial Intelligence Attack
Artificial Intelligence Attack is a new type of attack developed in our company. It is based upon a social engineering method and has never been implemented in password recovery applications.
This attack allows, without resort to time-consuming and costly computations, to almost instantly recover certain passwords encrypted with hash functions. The basic idea behind the AI attack is that an average user very often chooses similar words and word combinations or follows the same password generation rule when creating one’s passwords. With that in mind, we could attempt to figure that rule out and pick the original password.
Although this sounds somewhat abstractive, in the reality the attack clearly splits into four successive steps.
- Initiating the collection of private data. Here comes into action the password retrieval and indexation module, which looks for all available and hidden in the system passwords entered by a user at any moment of time. Those include network access passwords, ICQ, email, FTP, Windows account passwords, server passwords, etc.
- Launches the data collection and indexation module. During the execution of this step, we analyze the activity of the user (or all users, if the indexation module selected is different than Light) in the system. Next, based upon that, we generate the list of words - potential passwords selected from the text files, archives, internet browsers' history, email correspondence, etc.
- Includes the semantic analysis module for the database of found passwords and the list of potential passwords.
- On the final stage, the data analysis module will perform the mutation of the words and attempt to pick the passwords.
At the beginning of the attack, the program will search the system for all passwords it knows of. For that purpose, there are currently 32 mini-modules for decrypting system, mail, browser, messenger, archive and other passwords. Then there goes the file and data indexation, along with the course of which the program generates a potential attack dictionary. The third module breaks the passwords and words into pieces, out of which in the last module it will assemble new combinations for picking and guessing the original password.
On average, with the least indexation and mutation levels, the attack time may vary between 1 minute and 10-15 minutes, depending on the network activity of the user. On a home computer, the entire route normally takes not more than 2-3 minutes. Naturally, the more complex is the mutation and indexation level, the more efficient will be the search. However, reaching the topmost indexation and analysis level may take hours and even days, depending on the speed of the password validation algorithm and the number of users in the system. In the future, to cut the elapsed time, we are planning on including the multithreading support for engaging all cores of a processor.
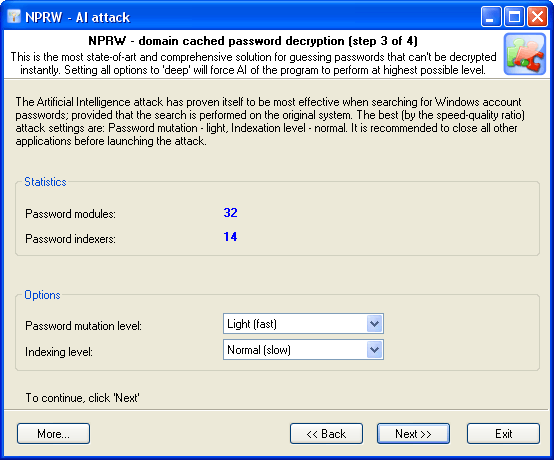
The Artificial Intelligence attack has proven itself to be most effective when searching for Windows account passwords; provided that the search is performed on the original system. The best (by the speed-quality ratio) attack settings are: Password mutation - light, Indexation level - normal. It is recommended to close all other applications before launching the AI attack.

