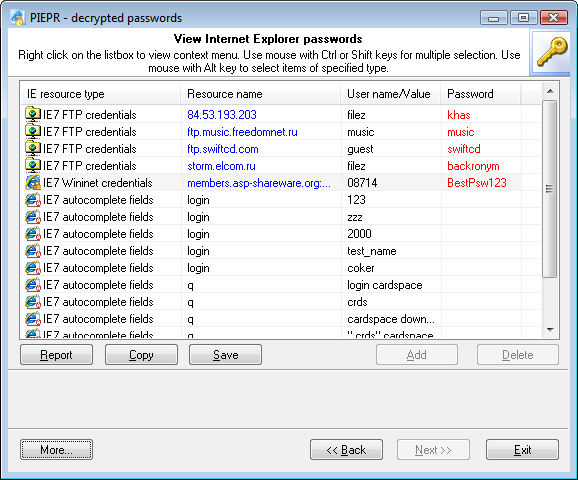
Recovering Internet Explorer 7 - 9 passwords
 posted by Passcape_Admin at 22:45:00 10.12.2009
posted by Passcape_Admin at 22:45:00 10.12.2009
Introduction
Step 1: Selecting the manual operating mode.
Step 2: Defining the data source.
Step 3: Recovering user's Master Key. Statistics on recovered passwords.
Step 4: Gathering encryption keys.
Step 5: Recovering data.
Introduction
Unlike its older brotherhood, the new version of Internet Explorer 7 (IE8 and IE9 have similiar protection scheme) utilizes absolutely different concepts of encrypting private data, without saving encryption keys. That makes it extremely difficult to recover such data, especially in the automatic mode. Therefore, to ensure the complete recovery of the password, we have added the manual operating mode to the application's Wizard as an alternative to the automatic recovery mode. More flexible and advanced, it uses some specially invented algorithms and allows extracting keys that are unavailable in the automatic mode.
The manual mode for IE7 passwords can be theoretically split into 5 parts or 5 steps of the PIEPR's Wizard. To be more accurate, there are just 4 steps, and during the first step you are to choose the operating mode itself.
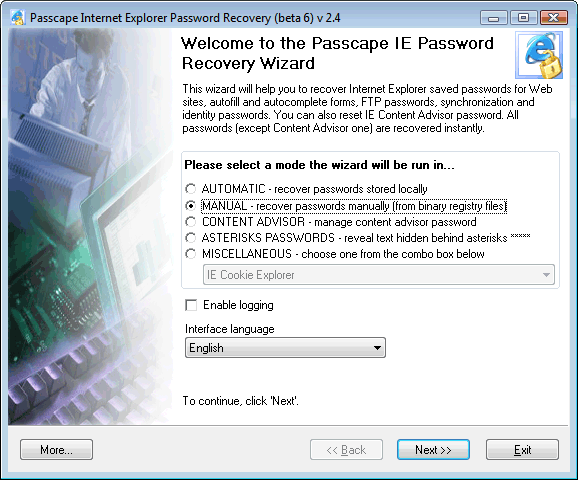
STEP 1: Selecting the manual operating mode
STEP 2: Defining the data source
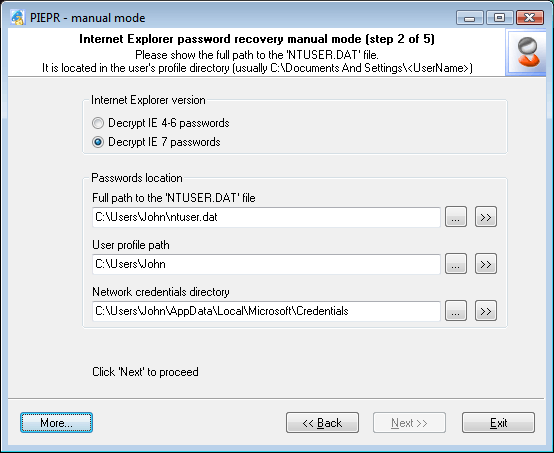
On this, second, step of the manual recovery, you will be prompted to enter the three parameters that are necessary to start the recovery process. Actually, the software will try to acquire all the necessary data automatically. However, if it fails to succeed, it will ask you to enter the necessary data by hand:
-
Path to user's registry file (ntuser.dat), which is located in the user's profile. User's registry is the main container that stores three types of encrypted Internet Explorer 7 passwords (there are totally 4 of those). In Windows XP-2003, path to this file normally looks like this: C:\Documents And Settings\%USER%\ntuser.dat, where %USER% stands for your account name. For Vista, the default path may look a bit different: C:\Users\%USER%\ ntuser.dat. This parameter is mandatory, and the further recovery is impossible unless this parameter is supplied.
-
Path to user's profile (optional parameter). The software normally detects it automatically by user's registry located in it (see above). User's profile folder is the starting point for the automatic detection of some other options that appear on the next step. If this parameter is not set, the recovery wizard will be unable to find out the path to user's Master Key on the third step, and the further recovery is only possible when that parameter is properly supplied.
-
Network Credentials Directory (optional). Windows Credentials Manager creates and controls this folder, storing many applications' private data in it. Those may include domain and LAN passwords, .Net Passport accounts, Exchange server passwords, different types of Authentication Credentials, etc. All of that data is encrypted and stored in Network Credentials Directory. In our case, we are particularly interested in IE7's Web passwords to protected websites, which are also known as Wininet Credentials. For more information on Wininet Credentials, please take a look at our article on Internet Explorer passwords. In Windows XP-2003, Wininet Credentials can be stored in two different folders:
C:\Documents And Settings\%USER%\Application Data\Microsoft\Credentials\%SID%
or
C:\Documents And Settings\%USER%\Local Settings\Application Data\Microsoft\Credentials\%SID%.
Please note that %USER% stands for your Windows account name, and %SID% is the SID of the user whose passwords are to be recovered. In Vista, SID is not used in the network credentials directory name, so the path to the encrypted Wininet Credentials data looks a bit different:
C:\Users\%USER%\AppData\Local\Microsoft\Credentials
and
C:\Users\%USER%\AppData\Roaming\Microsoft\Credentials.
Here is a couple of examples with real paths to Network Credentials Directory:
C:\Users\John\AppData\Local\Microsoft\Credentials
D:\Documents and Settings\Kate\Application Data\Microsoft\Credentials\S-1-5-21-1927147842-1992852531-225342917-1003.
It is very convenient to use the >> button to find out a local user's network credentials directory. When you click on that button, you will be prompted to choose the required local user's profile, and the software will automatically choose the Network Credentials Directory corresponding to that. If the data that were required for the recovery were taken from another computer, you will have to enter the path to Network Credentials Directory manually (by clicking on the ... button).
STEP 3: Recovering user's Master Key. Statistics on recovered passwords.
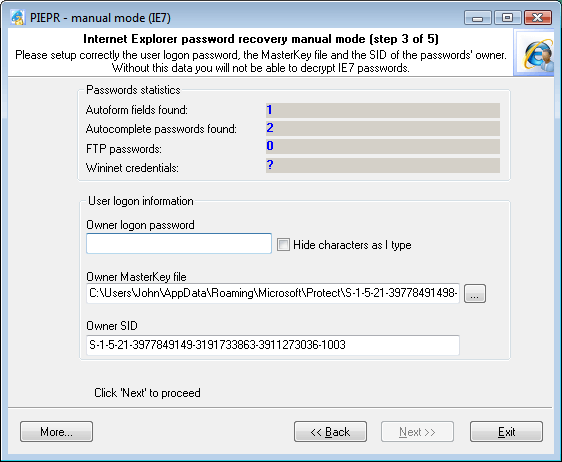
On the third step, the recovery Wizard that you have supplied with the necessary information will attempt to find out whether any Internet Explorer 7 passwords are available and how many of them are there. The Password Statistics section will display information on the found (but not yet recovered) passwords.
The software can find out the number of available Wininet Credentials only after you have:
- Entered a correct Network Credentials Directory parameter on the previous step of the recovery wizard.
- Filled all options in the User logon information section, including user's password.
Usually, the software automatically finds the Owner MasterKey file and Owner SID the parameters for a local user. However, you can specify those manually. By default, user's Master Key file is stored in the following folders:
Windows XP-2003: C:\Documents and Settings\%USER%\Application Data\Microsoft\Protect\%SID%
Windows Vista: C:\Users\%USER%\AppData\Roaming\Microsoft\Protect\%SID%
The text parameter Owner SID is normally the same as the %SID% folder name.
Once you have entered a correct password in the User logon information field, the software will count the number of Wininet Credentials, and the 'Next >>' button will be enabled, so you can go on to the next step of the Wizard - looking for encryption keys.
STEP 4: Gathering encryption keys
Gathering encryption keys is the most important and crucial moment in the entire recovery process. As it was mentioned before, the encryption mechanism in Internet Explorer 7 was purposely made up such way that whenever it is possible, the application would not store its encryption keys on the local computer. So, before you get started with searching and picking the keys, you will have to understand the IE's concept of operation used when encrypting passwords and form data. For now, you can forget about FTP and Wininet passwords, since on this, fourth step of the recovery wizard, the software has sufficient information to recover them completely.
So, the encryption algorithm for Autocomplete passwords in IE 7 looks as follows:
- During the first visit to the Web page, once user has entered the password, Internet Explorer saves the current page's URL and calculates a hash from that address hash=SHA(URL).
- The URL saved on the previous step (a Unicode-based text string) is used as the encryption key. This key is used for encrypting the password with strong encryption algorithms (DPAPI). EncryptedPassword=DPAPI(URL,password).
- The EncryptedPassword is linked to the hash, and both of those values are stored in the user's registry.
- The URL is purged as it is no longer necessary.
The only conclusion that comes from the above is that unless one knows the original URL, he will be unable to recover the password, for the reverse recovery of the URL from the hash is literally impossible. On the other hand, it is not at all necessary to store the encryption key (URL) on the local computer.
But then how does Internet Explorer recover its own passwords? - Well, very simply:
When the website is visited again, IE again calculates a hash from the URL. Then it verifies the obtained hash against all values (hash + EncryptedPassword) that are stored in the registry. If one of the hash values stored in the registry has matched, the encrypted password linked to that hash is recovered with the URL supplied as the corresponding key.
The encryption of Autoform data is implemented a bit different way. For example, if the authentication page has fields for entering login and password, the login is encrypted and stored different way than the password. The basic difference is that instead of the URL the software uses the field name in the HTML form for the encryption key. Let's take a look at an excerpt of an html file that contains a form for entering login and password.
<table><tr>
<td><input type="text" name="loginname" value=""><br></td>
<td><input type="password" name="pwd" value=""><br></td>
</tr></table>
In our case, the form field name and the encryption key will be the text value loginname. Other than that, the encryption mechanism for Autoform data is completely the same as the mechanism for encrypting password.
Therefore, for the complete recovery of Autoform fields and Autocomplete passwords in Internet Explorer 7 we have created such a tricky and not so clear at first user interface. The five tabs that you see on the screenshot are just the five methods that you can utilize to recover encryption keys (let us know if you know more). Those keys, in their turn, are required to recover the found passwords. The number of recovered passwords depends directly upon the efficiency of your actions on that step. So, here is a brief description of each method.
1. GUESS SIMPLE KEYS
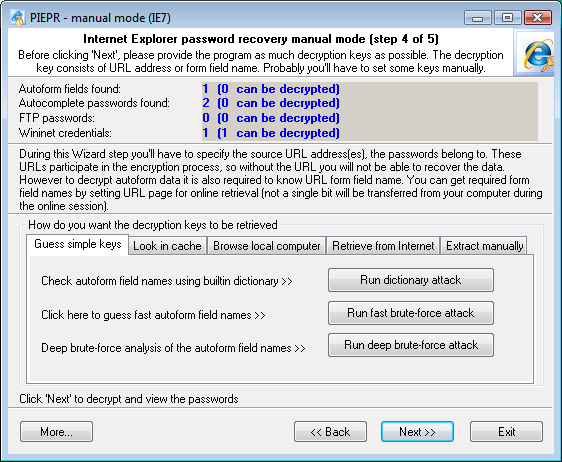
This method allows finding Autoform encryption keys using dictionary or brute-force attack. When you click on the Run Dictionary Attack button, the software will search for the keys using the built-in dictionary, which comes along with the application. If you want to use your own dictionary, just name it custom.dic and copy it to the program's installation directory. You can also attempt the brute-force attack, where the software will check the password against all possible combinations of letters and numbers. However, the major drawback of this method is that it can be efficiently used only for short (up to 6 characters) keys. In the next version of the software, we are planning to introduce a new type of attack using smart mutations.
2. SEARCH IN CACHE
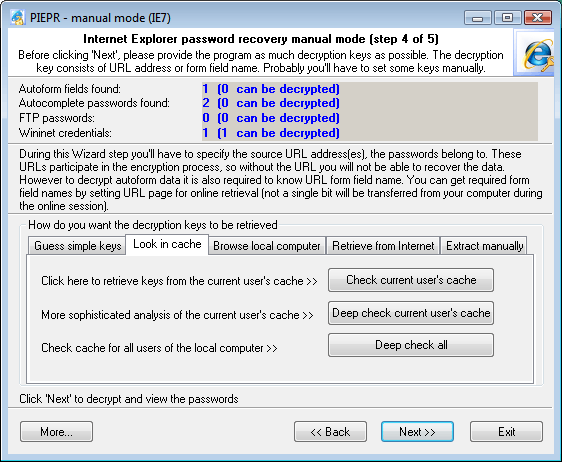
On this tab, you can attempt to find your lost Internet Explorer encryption keys (for both passwords and forms) in your local computer's cache. When you click on the Check Current User's Cache button, the application will launch the quick key search in the current user's cache. To launch the deep search, you will need to click on the Deep Check Current User's Cache button. Despite that it is slightly slower than the previous one its major advantage is that the search is performed independently of Windows API functions. However, the slowest but sometimes most efficient method for finding Autoform keys is the third search type (Deep Check All), where the search is performed in all users' cache on the local computer.
3. BROWSE LOCAL COMPUTER
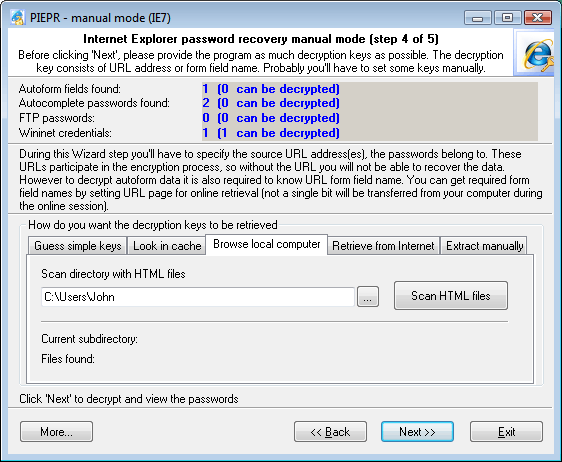
This tab only allows finding encryption keys for Autoforms. To go on with this method, you will need to specify the path to the folder with HTML files. It doesn't matter what kind of files those are; the idea is to get as many files as possible. Such folder, alternate to Internet Explorer cache, for example, could be a folder with html files from another browser. For example, Opera stores (caches) all visited pages to a special location (normally C:\Documents and Settings\%USER%\Application Data\Opera\Opera\profile\cache4). Once such folder has been specified, you can get started with scanning the HTML files and verifying all the found form field names. These names very often match those that you are to find.
4. RETRIEVE FROM INTERNET
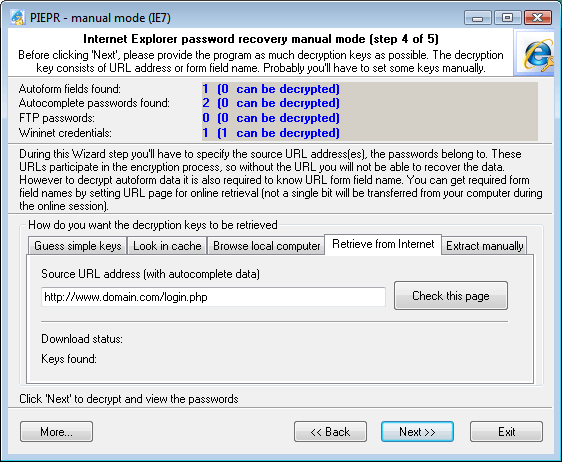
If you've got any passwords still not recovered (the statistics appears at the top of the dialog window), this tab will be your last source of hope. Enter the URL of the page (you can copy it from your browser's Address line), which you are to recover the passwords for, and then click Check this page. The software will attempt to perform two things. First, it will check whether the URL is good as the key for the remaining Autocomplete passwords. Then it will attempt to download the specified page off the Internet to check it for the Autoform keys. In the next versions, the software will possibly support URL lists.
5. MANUAL RECOVERY
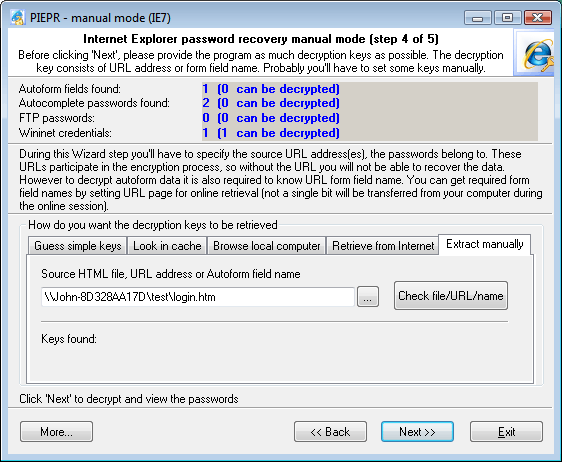
Finally, the last tab for a despaired paranoiac.
You don't have to be connected to the Internet to get started with it. However, you can specify:
- HTML file – for searching Autoform encryption keys
- URL address – for verifying Autocomplete passwords
- Name of a specific field on the HTML form – to verify Autoform encryption keys.
The tabs follow one another according to their efficiency. The most efficient method for finding keys is dictionary attack on the Guess simple keys tab. It is followed by the search in Internet Explorer cache, processing html files, retrieving from the Internet, and, finally, manual recovery. If you've got at least one still not recovered password, try all these recovery methods before clicking 'Next >>'.
STEP 5: Recovering data
On the final step, the Wizard will analyze all the obtained keys and recover the original encrypted data.