Windows Password Recovery - Windows Hello credentials
This feature is aimed to locate and decrypt plaintext credentials stored by Windows Hello. Windows hello uses Next Generation Cryptography (NGC or also called CNG) to protect and store user private data and encryption keys. Even though NGC is very elaborated and sophisticated system (worth mentioning that it uses even some undocumented trick to protect encryption keys and data), Passcape software was first, just like in case of DPAPI, who managed to create the almost identical set of APIs but with support for offline mode. Yes, the tool can be used both for a living system and for any external OS. That makes it easy to work with the program even for a newbie, leaving all the numerous and routine operations to the program.
Setting Windows directory
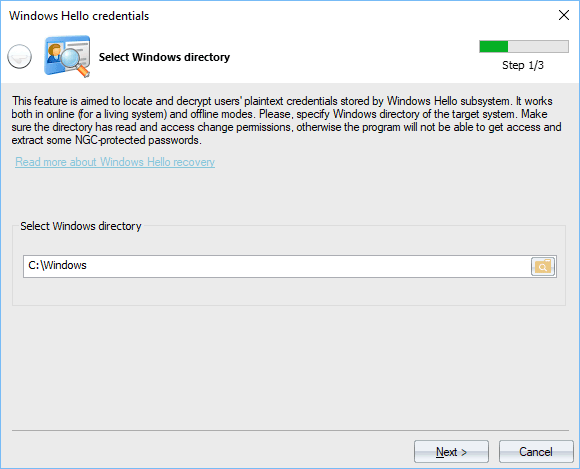
The working mode is detected automatically once a Windows directory is set. The Windows folder holds files and encryption keys protected from being accessed to even by Administrators. To extract the keys, this folder should permit access change or file write operations. Otherwise, the program will not be able to decrypt passwords encrypted with NGC.
Selecting data to decrypt
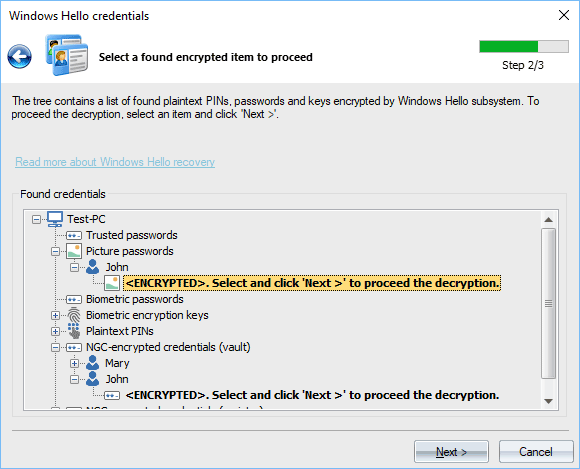
During this step, the program outputs all found but not yet decrypted credentials, keys, PINs. Definitely, Windows Hello was developed by several development teams, because multiple encryption subsystems are used and all personal data are scattered through the whole system. Currently, the program supports the following data types:
- Picture passwords
- Logon plaintext passwords protected with picture passwords
- Biometric credentials
- Logon plaintext passwords protected with biometric credentials
- Biometric encryption keys
- Plaintext PINs
- PIN history
- Logon plaintext passwords, stored in Windows Vault and protected by NGC
- Logon' plaintext passwords, stored in Windows registry and protected by NGC
To finalize the decryption, just double-click an item in bold.
Decrypted picture password
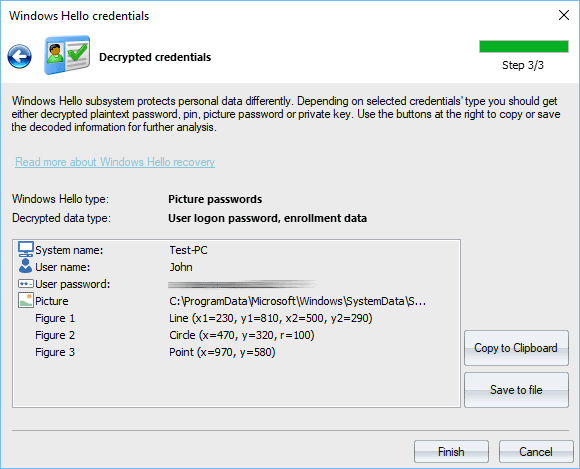
Decrypted logon password (hidden here) and picture password.
Your picture password is poorly protected and can be easily decrypted and viewed by anyone who has physical access to your PC. Avoid using it on Windows 8-10 systems.
Decrypted PIN
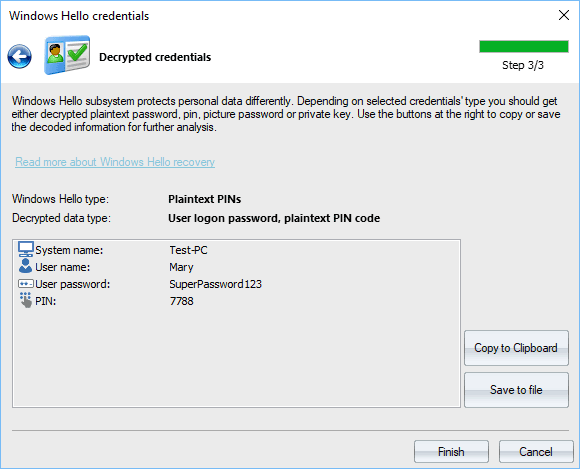
Decrypted logon password and PIN code.
Decrypted logon password
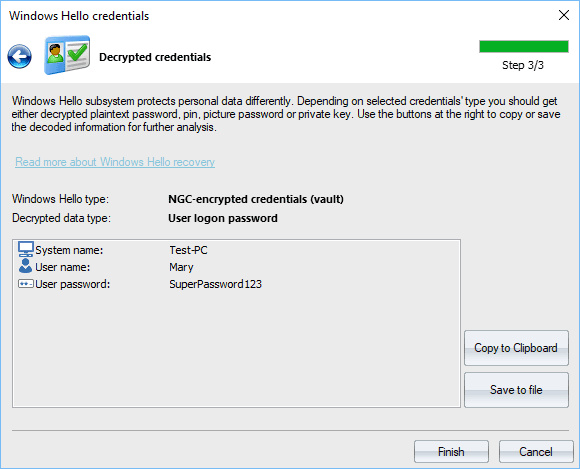
Decrypted logon password for user 'Mary'.
Note that plaintext passwords protected with NGC can be decrypted using either a biometric key or a PIN. The program first tries to locate biometric keys and if it fails to (for example, the biometric logon has not been set), Windows Password Recovery prompts for a PIN in order to be able to finalize the decryption.
To recover Windows Hello credentials protected with TPM you should run the program on the same computer where the TPM chip is installed.





