Reset Windows Password v14.2
Telegram data recovery, Photo Database and Media Player investigation tools, and some more
Reset Windows Password v14.1
IP addresses history viewer, fast disk search, local security editor and some more
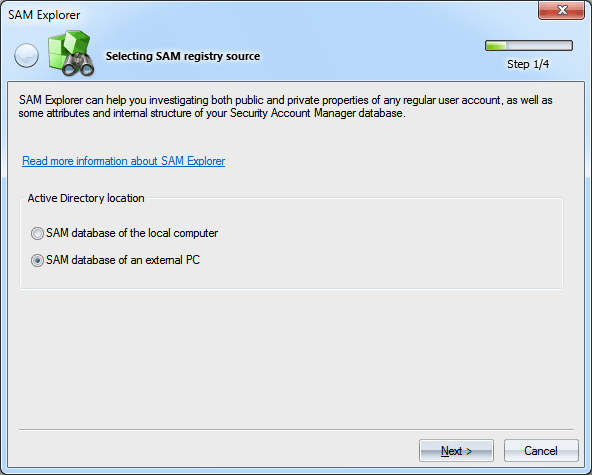
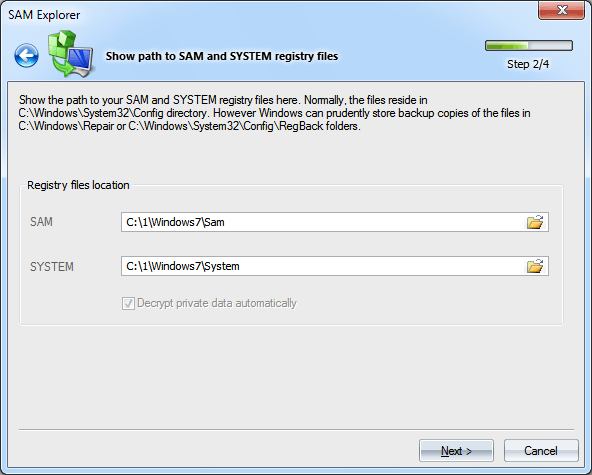
Windows Password Recovery - SAM explorer
Please note: if you select a local database, for safety reasons, the editor will not be available, and the database will open in the read-only mode.
DataRevision
32-bit unsigned integer that stores version of the data structure. It is divided into 2 WORDs: version major and version minor. LastLogon
A 64-bit value, equivalent to a FILETIME, indicating the time at which the account last logged on. LastLogoff
A 64-bit value, equivalent to a FILETIME, indicating the time at which the account last logged off. PasswordLastSet
A 64-bit value, equivalent to a FILETIME, indicating the time at which a password was last updated. AccountExpires
A 64-bit value, equivalent to a FILETIME, indicating the time at which an account is no longer permitted to log on. LastBadPasswordTime
A 64-bit value, equivalent to a FILETIME, indicating the time at which an account last tried to logged on unsuccessfully. UserID
A 32-bit unsigned integer representing the RID of the account. PrimaryGroupId
A 32-bit unsigned integer indicating the primary group ID of the account. UserAccountControl
A 32-bit flag specifying characteristics of the account. The following values are attributes of a user account and can be combined by using a bitwise OR operation:
CountryCode
A 16-bit unsigned integer indicating a country preference specific to this user. The space of values is the international country calling code. For example, the country code of the United Kingdom, in decimal notation, is 44. CodePage
A 16-bit unsigned integer indicating a code page preference specific to this user object. The space of values is the Microsoft code page designation. BadPasswordCount
A 16-bit unsigned integer indicating the number of bad password attempts. LogonCount
A 16-bit unsigned integer indicating the number of times that the user account has been authenticated. AdminCount
A 16-bit unsigned integer indicating that the account is a member of one of the administrative groups (directly or transitively). OperatorCount
A 16-bit unsigned integer indicating that the account is a member of the Operators group. UserName
Unicode string that specifies the name of the user account. FullName
Unicode string that contains the full name of the user. AdminComment
Administrator comment associated with the user account. UserComment
Second user comment associated with the user account. Parameters
Extended user parameters. Microsoft products use this member to store user configuration information. HomeDirectory
Unicode string specifying the path of the home directory for the user account. HomeDirectoryDrive
Specifies the drive letter to assign to the user's home directory for logon purposes. ScriptPath
Unicode string specifying the path for the user's logon script file. The script file can be a .CMD file, an .EXE file, or a .BAT file. ProfilePath
Unicode string that specifies a path to the user's profile. WorkStations
Unicode string that contains the names (separated by commas) of workstations from which the user can log on. Up to eight workstations can be specified. The account flag UF_ACCOUNTDISABLE allows disabling logons from all workstations to this account. LogonHours
21-byte bit string that specifies the times during which the user can log on. Each bit represents a unique hour in the week, in Greenwich Mean Time. The first bit is Sunday, 0:00 to 0:59; the second bit is Sunday, 1:00 to 1:59; and so on. Note that bit 0 in word 0 represents Sunday from 0:00 to 0:59 only if you are in the GMT time zone. In all other cases you must adjust the bits according to your time zone offset (for example, GMT minus 8 hours for Pacific Standard Time). Groups
List of groups to which the user account belongs or does not belong. LMHash
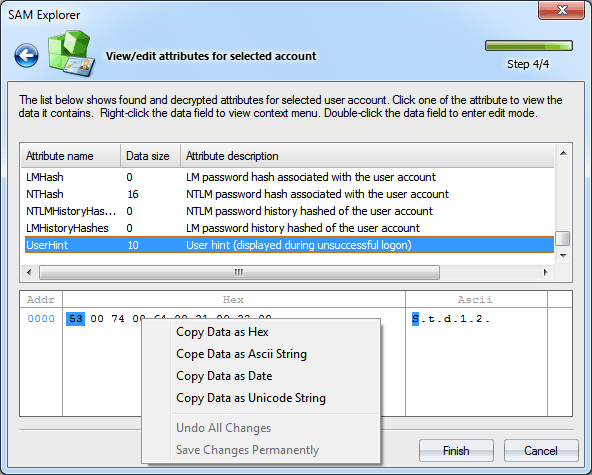
LM password hash associated with the user account. NTHash
NTLM password hash associated with the user account. LMHistoryHashes
LM password history hashed of the user account. NTHistoryHashes
NTLM password history hashed of the user account. UserHint
User hint (displayed during unsuccessful logon). UserPicture
Logon picture associated with the account. | |||||||||||||||||||||||||||||||||||||||||||||