Reset Windows Password v14.2
Telegram data recovery, Photo Database and Media Player investigation tools, and some more
Reset Windows Password v14.1
IP addresses history viewer, fast disk search, local security editor and some more
Windows Password Recovery - hybrid dictionary attack using GPU
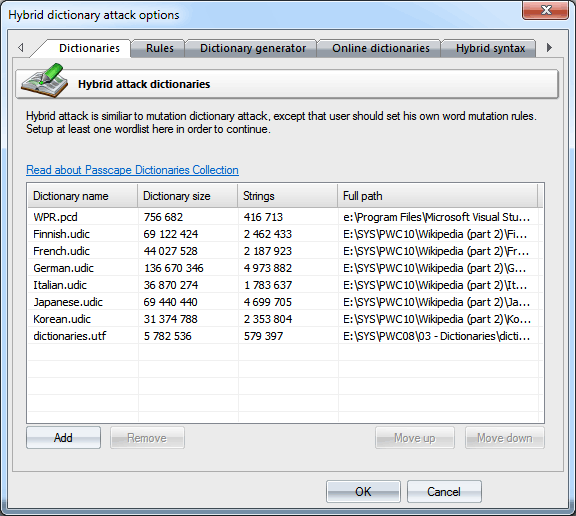
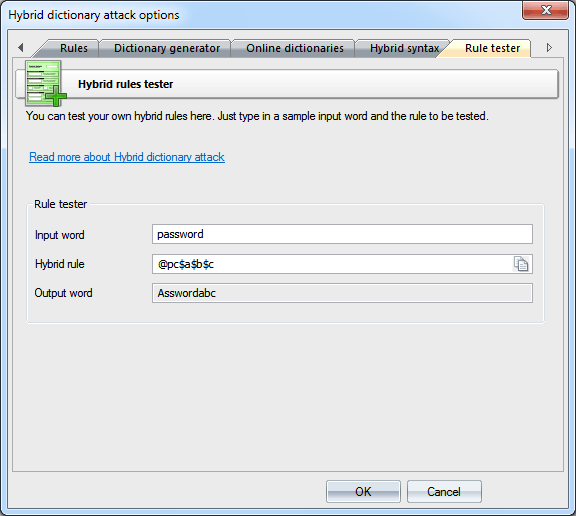
DictionariesWordlists to be used in the attack are set on the first tab. Traditionally, the application supports wordlists in ASCII, UTF8, UNICODE, PCD, RAR and ZIP format. The position of the files on the list can be altered. For example, you may want to move smaller dictionaries up the list or the other way. During the attack, they will be used one after another, according to their position on the list.
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Rule | Example | Input | Output | Description |
| : | : | password | password | Do nothing to the input word. |
| { | { | password | asswordp | Rotate the word left. |
| } | } | password | dpasswor | Rotate right. |
| [ | [ | password | assword | Delete the first character. |
| ] | ] | password | passwor | Delete the last character. |
| c | c | password | Password | Capitalize. |
| C | C | password | pASSWORD | Anti-capitalize - lowercase the first character, uppercase the rest. |
| d | d | password | passwordpassword | Duplicate word. |
| f | f | password | passworddrowssap | Reflect word. |
| k | k | password пароль |
зфыыцщкв gfhjkm |
Convert word using alternative (first after default) keyboard layout. The rule works in both directions. For example, if there's Russian keyboard layout installed previously in the system, the rule should convert word 'password' to Russian 'зфыыцщкв', and Russian word 'пароль' to 'gfhjkm'. This is very helpful when looking for non-English passwords. If only one language is installed in the system, the rule does nothing. |
| K | K | password | passwodr | Swap last two characters. |
| l | l | PassWord | password | Convert all characters to lowercase. |
| q | q | password | ppaasssswwoorrdd | Duplicate all symbols in a word. |
| r | r | password | drowssap | Reverse word. |
| t | t | PassWord | pASSwORD | Toggle case of all characters |
| u | u | password | PASSWORD | Convert to uppercase. |
| U | U | my own password | My Own Password | Capitalize all words delimited with space (upper-case the first character and every character after space). |
| V | V | password | PaSSWoRD | Vowels elite. |
| v | v | password | pASSWoRD | Vowels noelite. |
| 'N | '4 | password | pass | Truncate the word to N character(s) length. |
| +N | +1 | password | pbssword | Increment character at position N by 1 ASCII value. |
| -N | -0 | password | obssword | Decrement character at position N by 1. |
| .N | .4 | password | passoord | Replace character at position N with character at position N+1 |
| ,N | ,1 | password | ppssword | Replace character at position N with character at position N-1. Where N > 0. |
| <N | Reject (skip) the word if it is greater than N characters long. | |||
| >N | Reject (skip) the word if it is less than N characters long. | |||
| _N | _8 | Reject (skip) the word if its length is not N. | ||
| aN | a8 | Check all possible symbol cases for the word. N is a maximal length of the word to apply this rule for. | ||
| DN | D2D2 | password | paword | Delete the character at position N. |
| pN | p3 | key | keykeykey | Copy word N times. |
| SLN | SL2 | 012345678 | 01d345678 | Bitwise shift left character at position N. |
| SRN | SR2 | password | pa9sword | Bitwise shift right character at position N. |
| TN | T1T5 | password | pAsswOrd | Toggle case of the character at position N. |
| yN | y3 | password | paspasword | Duplicate first N characters. |
| YN | Y3 | password | paswordord | Duplicate last N characters. |
| zN | z3 | password | ppppassword | Duplicate the first character of the word N times. |
| ZN | Z3 | password | passwordddd | Duplicate the last character of the word N times. |
| $X | $0$0$7 | password | password007 | Add character X to the end of the word. |
| ^X | ^3^2^1 | password | 123password | Insert character X at the beginning of the word. |
| @X | @s | password | paword | Remove all characters X from the word. |
| !X | !. | Reject (skip) the word if it contains at least one character X. | ||
| /X | /1/2/3 | Reject (skip) the word if it does not contain character X. | ||
| (X | (p | Reject (skip) the word if the first character is not X. | ||
| )X | )d | Reject (skip) the word if the last character is not X. | ||
| eX | e@ | mike@yahoo.com | mike | Extract a substring starting at position 0 and ending up before the first occurrence of X character (do nothing if X is not found). |
| EX | E@e. | mike@yahoo.com | yahoo | Extract a substring starting right after first found X character and till the end of the string (do nothing if X is not found). |
| %MX | %20 | Reject (skip) the word if it does not contain at least M instances of the character X. | ||
| *XY | *15 | password | possward | Swap characters at positions X and Y. |
| =NX | =01 | Reject (skip) the word if the character at position N is not equal to the X | ||
| iNX | i4ai5bi6c | password | passabcword | Insert the character X in position N. |
| oNX | o4*o5* | password | pass**rd | Overwrite a character in position N with the character X. |
| sXY | ss$so0 | password | pa$$w0rd | Replace all characters X with Y. |
| xNM | x4Z | password | word | Extract a substring of up to M characters length, starting from position N. |
| INX-Y | rI0/-/r | google.com | google.com/ | Insert the character X at position N if the previous character at position N is not Y. |
| INX+Y | rI0.+.r | password. | password.. | Insert the character X at position N if the previous character at position N is Y. |
| ONX-Y | O0-+p | password | -assword | If the character at position N is not Y, overwrite it with X character. |
| ONX+Y | O0P+p | password | Password | If the character at position N is Y, overwrite it with X character. |
| RNM+Y | R01+a | password | assword | Remove character at position N if the character at position M is Y |
| RNM-Y | R40-b | password | passord | Remove character at position N if the character at position M is not Y |
| ?iN[C] | ?i0[digits] | password | 0password .. 9password |
Insert a character from a charset [C] into position N of the word. Where C should be either a predefined charset name or a custom character set itself. |
| ?iZ[C] | ?iZ[digits] | password | password0 .. password9 |
Insert a character from a charset [C] into the last position of the input word. |
| ?i[C] | ?i[special] | password | ~password .. password+ |
Insert a character from a charset [C] into every position of the word. [C] should be either a predefined charset name or a custom character set itself. |
| ?oN[C] | ?o1[upperalpha] | password | pAssword .. pZssword |
Overwrite a character at position N with a character taken from the charset [C]. Where C should be either a predefined charset name or a custom character set itself. |
| ?oZ[C] | ?oZ[upperalpha] | password | passworA .. passworZ |
Overwrite a character at the last position with a character taken from the charset [C]. |
| ?o[C] | ?o[-=.] | password | -assword .. password. |
Overwrite a character at every position of the word with a character taken from a charset [C]. Where C should be either a predefined charset name or a custom character set itself. The given example (?o[C] rule for the word password) will generate the following combinations: -password, =password, .password, -assword, =asswords, .assword, p-ssword, p=ssword ... password. |
GPU settings
Before launching the attack, make sure you setup up the GPU settings properly.
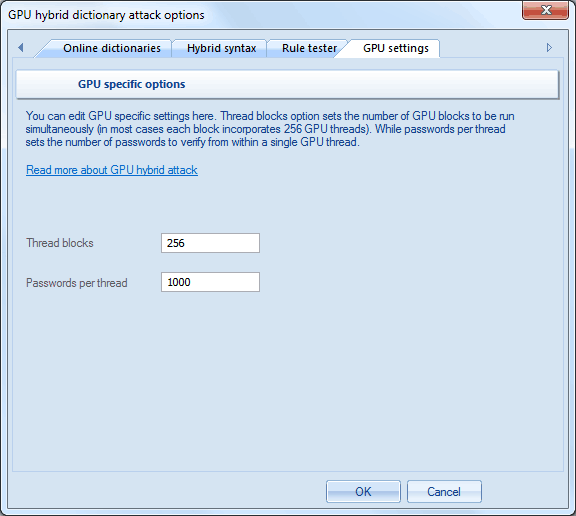
GPU configuration is pretty simple and consists of two parameters:
- The number of GPU blocks to be run at a single call to GPU. Each block consists of 256 threads. Thus, if you set the number of blocks to 256, the GPU will run 256*256=65536 threads. The total number of checked passwords for one call to GPU kernel will be 256*ThreadBlocks*PasswordsPerThread. In our case 256*256*1000 = 65 536 000 passwords per one call to GPU.
- The number of passwords to be sought in a single GPU thread. The greater the value, the lower the overhead associated with launching threads, and the higher the search speed. However, setting too great a value may hang the computer, make your GPU unresponsive or cause significant fluctuations in the current search speed, displayed on the status tab.