Windows Password Recovery - DPAPI blob decryption
The decryption of DPAPI blobs consists of four steps of the wizard.
Select DPAPI-encrypted blob file
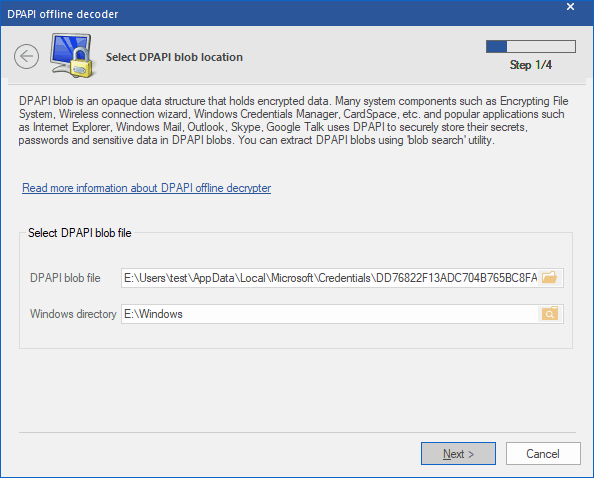
On the first step, specify the path to the file with a DPAPI blob. It is worth mentioning that actual DPAPI objects may be stored in different locations within the operating system; for example, in individual XML files, in the registry, in Active Directory; and in different formats: binary, ASCII, UNICODE. There is a special tool for locating, extracting and saving DPAPI blobs to files. With that utility, for example, you can save all DPAPI blobs from a user's registry to individual files and use them in the program. In order to decrypt data, you will also have to set up the Windows directory of the target drive.
Here are storage locations for some DPAPI objects.
- Internet Explorer and Outlook passwords, WiFi passwords (XP only): user's registry, %APPDATA%\ntuser.dat
- Google Chrome: %LOCALAPPDATA%\Google\Chrome
- WiFi passwords (Windows Vista and higher): %PROGRAMDATA%\Microsoft\Wlansvc
- Network connection passwords (Windows Credential Manager): %LOCALAPPDATA%\Microsoft\Credentials or %APPDATA%\Microsoft\Credentials
Select Master Key
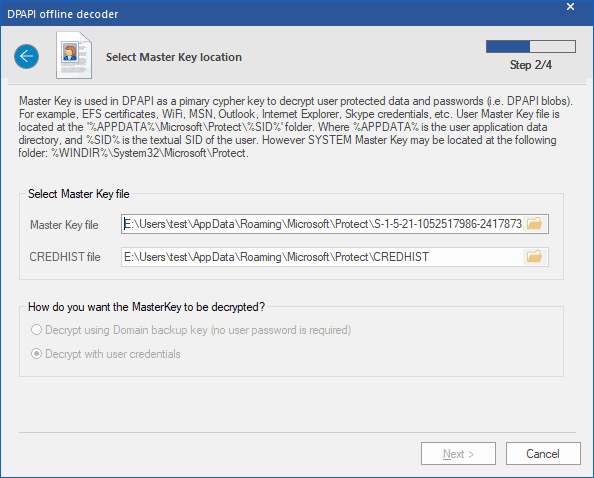
Master Key is a set of 64 random bytes, used as the primary key when decrypting DPAPI blobs. Master Key is encrypted with the user's password (or system's password if that is a system Master Key). User's Master Key is always located in %APPDATA%\Microsoft\Protect\%SID% folder, while a system account's Master Keys are stored in %SYSTEMDIR%\Microsoft\Protect. A typical user account holds several Master Keys, and only one of them is suitable for decrypting a certain object, the one with the name stored inside the DPAPI blob. When searching for a Master Key, the program may filter out unnecessary names. The folder %APPDATA%\Microsoft\Protect also contains the CREDHIST file, which is an optional parameter, and in most cases is not required for the decryption.
Decrypt Master Key
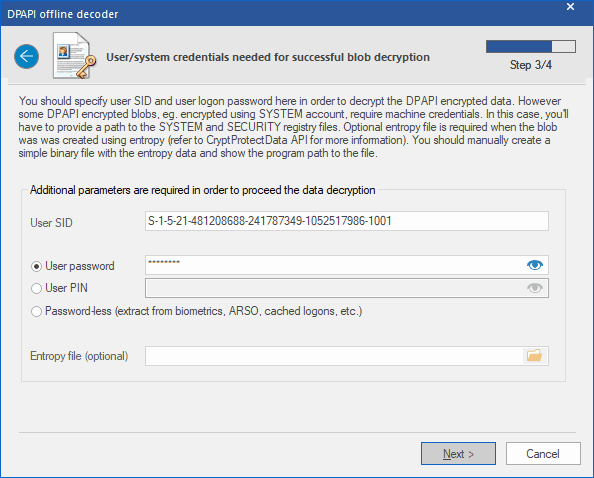
At least two parameters must be set in order to decrypt the user's Master Key: user's logon password and his security identifier (SID), which is normally specified in the path to the Master Key or flashed in CREDHIST. One way or the other, Windows Password Recovery calculates the user's SID automatically. To decrypt a system's Master Key, as it has been said already, setting a password makes little sense, as the program retrieves all data necessary for the recovery from two registry files: SYSTEM and SECURITY. If an additional entropy was used during blob creation, you must manually create the binary file that holds the entropy data and specify the path to it. For example, when encrypting Internet Explorer passwords, the UNICODE-formatted website name is used as entropy.
It is curious that Windows 2000 has a critical vulnerability, which allows decrypting any(!) DPAPI blob on a standalone PC without specifying the user logon password! I.e. All the data protected by the DPAPI are actually vulnerable. This is a major fault in the implementation of DPAPI, which is known to Microsoft; however, other operating systems do not have this drawback. If the CRYPTPROTECT_LOCAL_MACHINE flag was set in the CryptProtectData function when protecting data, the decryption of that data is also possible without the user's logon password (for example, wireless network passwords). However, this is a peculiarity of an interface implementation and is not a bug.
Windows Password Recovery starting with version 9.7 uses some new
vulnerabilities in the DPAPI Master Key protection which were revealed by our company. Thus, to decrypt a Master Key of a domain user, the owner logon password is not necessary any longer.
WPR v15 got a couple of new ways to decrypt a DPAPI blob. You can do it using the owner PIN or even with no PIN or password at all. Once the program detects that the user account is using Windows Hello biometric logon,
ARSO, cached passwords, etc. that it uses the data to unlock the protection without the need of a PIN or a password at all!
Decrypt data
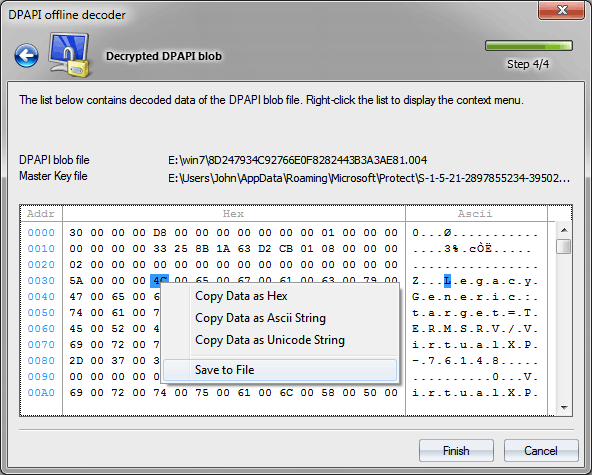
Having all that is necessary, Windows Password Recovery performs the final decryption of the DPAPI blob data, which you can then copy to clipboard or save to file. If the final step of the decryption ends up with an error, it is most likely because you have not set properly or not set at all the additional entropy. For example, Internet Explorer and Vista Ftp Manager use the source page, where the password was entered as entropy. Windows Credential Manager, similarly, uses certain string constants, and so on.




