Mask attack
Often the mask attack used if there's some information about the password to recover. For example, you know that the password begins with 'loveme' and followed by a word or a name. You can then set the following mask 'loveme%c%c%c%c%c%c' to check all possible variants from 'lovemeaaaaaa' to 'lovemezzzzzz'.
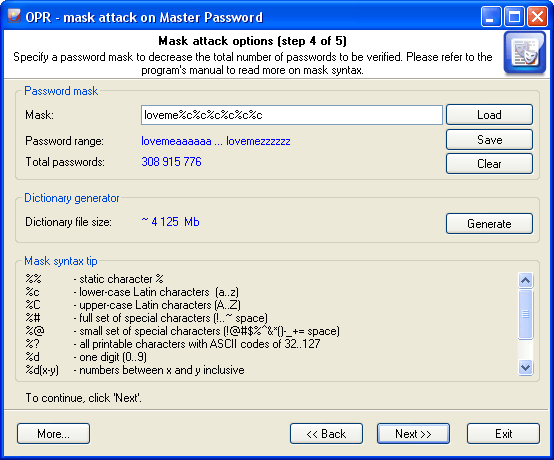
The mask entry field is used for setting the rule, by which the program will try to recover the password. If the mask is set correctly, below you will see the range of characters generated by the mask. User-defined masks can be saved to disk. You can also use the mask tool to generate a dictionary.
The password mask consists of static not changing characters and special sets - dynamically changing letters, numbers or symbols. For example, in the mask 'secret%d(1-100)', the characters 's' 'e' 'c' 'r' 'e' 't' are static, and '%d(1-100)' is the dynamical set. A dynamical set is always marked with % character.
The program supports the following dynamical sets:
| Dynamical set |
Description |
| %c |
lower-case Latin characters (a..z), 26 symbols |
| %C |
upper-case Latin characters (A..Z), 26 symbols |
| %# |
full set of special characters (!..~ space), total 33 symbols |
| %@ |
small set of special characters (!@#$%^&*()-_+= space), 15 symbols |
| %? |
all printable characters with ASCII codes of 32..127 |
| %d |
one digit (0..9) |
| %d(x-y) |
numbers between x and y inclusive |
| %r(x-y) |
user-defined characters with serial ASCII codes between x and y |
| %r(x1-y1,x2-y2...xn-yn) |
set of several non-overlapping sequences of ASCII characters. Useful for defining custom character sets; e.g., of OEM characters. |
| %l(n) |
link to another set from mask, 1 based |
| %% |
standalone static character % |
When setting %r, keep in mind that the range of defined OEM characters (with character code greater than 127) is generated using the DOS encoding.
Examples:
test%d - will generate password range test0..test9, 10 passwords total
test%d(1980-2007) - test1980..test2007, 28 passwords
test%r(48-57,97-122) - test0..testz, 36 passwords
%#test%# - _test_..~test~, 1089 passwords
%d(1-12)%r(45-47)%d(1-31)%l(2)%d(1980-2010) - 1-1-1980..12/31/2010, 34596 passwords
%c%r(32-63)%c%l(2)%c%l(2)%c - a_a_a_a..z?z?z - 14623232 passwords

