Windows Password Recovery - fingerprint attack
Fingerprint attack is a relatively new tool for recovering complex passwords, which could not be decrypted by other attacks. The idea of the attack is that here, to recover a password, we take neither individual words from the source dictionary, like in the dictionary attack, nor even word combinations, like in the combined attack, but so-called "fingerprints". Now, every source word from the dictionary is used for generating several fingerprints. If some password is found during the attack, it participates in generating new fingerprints, and the attack goes another round.
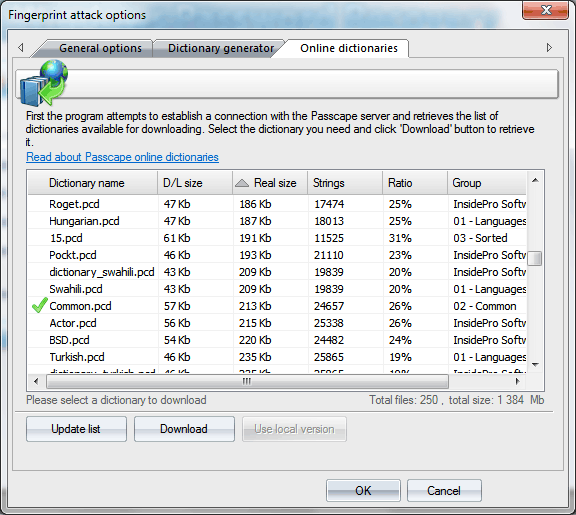
Before launching the attack, specify the source dictionary to be used for creating the fingerprint bank. The software comes with a dictionary, common.pcd, optimized for this attack, but you can use yours or download one off the Internet ('Online dictionaries' tab). There are no certain requirements to the dictionary, except one: the source dictionary must not be too large; otherwise, the attack will take significant time. You can use dictionaries with national passwords if you suspect that the sought password contains characters in a national encoding.
Here is the way to generate fingerprints: first, break each word from the source dictionary into one-character passwords, then - into 2-character, etc. For instance, break the source word crazy into one-character fingerprints. We get:
c
r
a
z
y
Now, two-character:
cr
ra
az
zy
Next, three-character:
cra
raz
azy
And, finally, four-character:
craz
razy
We have got 5+4+3+2=14 fingerprints, not counting the source word.
Repeat this for each word of the source dictionary. After this, all the fingerprints are dumped into a single database, naturally, discarding duplicates. We have got a database of fingerprints that would be used for checking passwords by gluing all the fingerprints with each other and finding the match.
The real fingerprint generation algorithm is much more sophisticated. Moreover, there is an option in the attack settings, Maximize efficiency when generating fingerprints, which uses a more sophisticated algorithm, which maximizes the efficiency (at the expense of speed) by generating additional fingerprints.
Let's take a look at the remaining options.
- Use PPP engine to generate additional passwords - use passwords found in other attacks when generating fingerprints.
- Use keyboard and frequently used sequences - add keyboard combinations and common sequences to fingerprint bank.
- Use dates - add dates to fingerprints.
- Use numbers and common sequences - use digits and simple combinations of letters.
The most careful attention should be paid to the option Loop until no more passwords are found. That is where fingerprint attack can really show itself off. Here is how it works: if at least one password is found during an attack when the attack is over, the password participates in generating new fingerprints, and the attack runs again. This option works great on large lists of hashes and on password history hashes.
The second tab with the settings allows to create and record a custom dictionary using the current options of fingerprint attack. Be careful; that dictionary may take up a lot of space on your computer's hard disk.
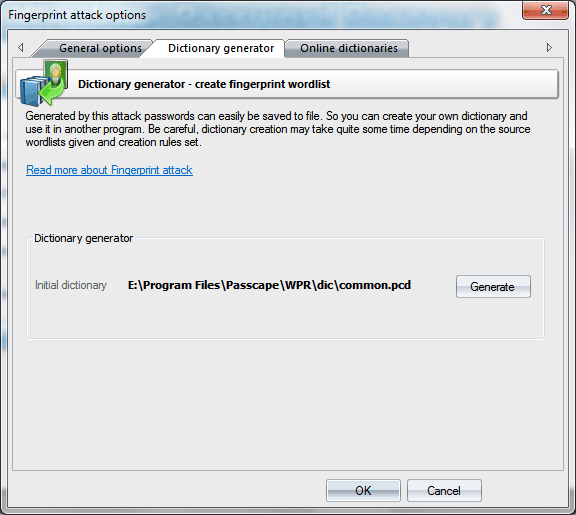
On the third tab, you can download source dictionaries for fingerprint attack from the Internet.