Windows Password Recovery - GPU dictionary attack
Oftentimes, when creating passwords, users add certain characters at the beginning, end or even middle of the word. To recover passwords of this specific kind, we have come up with a GPU-based dictionary attack, which is something between simple dictionary attack and brute force attack.
This attack works as follows:
- Reads the first word from the dictionary.
- According to the defined character set and the minimum/maximum length of the search range, generates all the possible variants.
- Those variants (characters) are then added to the beginning, end or middle of the word. The position within the word, where the generated sequences are to be inserted, can be specified at your discretion.
- Then goes the next dictionary word, etc.
For example, if we specify a search character range between 0 and 9, and the range length between 1 and 2, the program will generate 100 combinations: 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11 .. 99. Then these sequences will be added to the beginning, middle or end of the word. Thus, for the word test, if the sequences are going to be inserted to every listed position, the program will check the following passwords:
0test, 1test .. 99test
t0est, t1est .. t99est
te0st, te1st .. te99st
tes0t, tes1t .. tes99t
test0, test1 .. test99
Total - 100*5=500 variants.
Let's take a closer look at the attack settings.
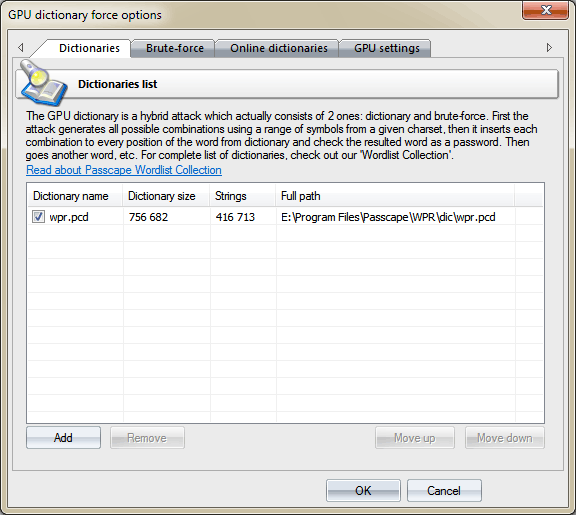
Dictionaries
On the Dictionaries tab, you can specify the list of dictionaries to be used in the attack. The program supports text wordlists in the following formats: ASCII, UNICODE, UTF8, RAR, ZIP, as well as encrypted/packed dictionaries in the native PCD format, developed by our company. To deactivate a dictionary, simply clear the checkbox by its name. Thus, although the dictionary remains on the list, it will be ignored by the attack. The software comes with the default 400000-word dictionary. You can order the full set of dictionaries, that’s over 7.5 GB in size, on CD or take advantage of our dictionaries available online.
Search range
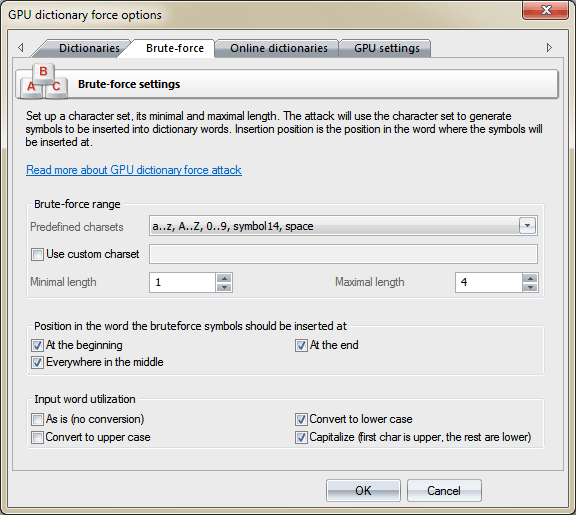
On this tab, you should set up the range of characters to be inserted into base words, its minimum and maximum length. When setting up a range, you can use the existing templates or, having checked the respective checkbox, define your own one. When selecting the maximum range length, keep in mind that specifying a too wide or too small value is inadvisable. While in the first case the password search speed may drop down to 0, specifying a too narrow range of characters to be searched raises the overheads related to the irrational use of the computing power of the GPU.
In the second group of options, specify the position in the word, where the characters of the searched range would be inserted.
And, finally, the third group of settings - these are in charge of preprocessing the words from the source dictionary. Selecting the As is option makes the program use the source word as is, not converting to upper or lowercase. The number of passwords to be searched grows in direct proportion to the number of options specified in this group. On the other hand, the program is smart enough to not use repeat words. For example, the word 12345678, even if all the conversion options are set, will be used only once.
The number of passwords to be searched for a single word can be calculated using the following formula:
passwords = R * L * K
where
R - character range, calculated using the formula: R = charset_length ^ max_length - charset_length ^ (min_length-1) +1
L - positions in the word. Calculated as follows: if the insertion is made in the middle of the word, L = password_length - 1; then add plus one if the insertion is made to the beginning and end of the word.
K - the number of options specified in the group 'Input word utilization'.
For example, if the source word we have is window, and the options are specified as shown on the image above, i.e. character range a..z,A..Z,0..9,symbol14,space, insertion to all positions, conversion to lowercase and capitalizing (first letter in uppercase). Let's calculate how many password we are going to check for this word:
charset_length = 26+26+10+14+1 = 77
R = 77^4 - 77^0 + 1 = 35153041
L = (6-1) + 1 + 1 = 7
K = 2
passwords = 35153041 * 7 * 2 = 492 142 574
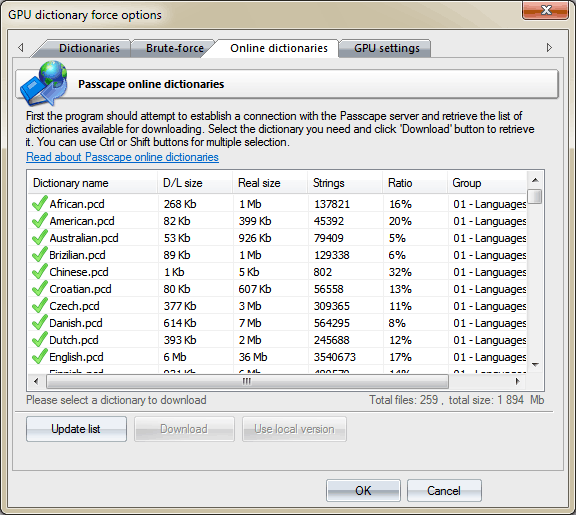
Online dictionaries
On the third tab, you can download source wordlists for the attack. The program uses internal wordlist (400000+ words) by default.
GPU settings
Before you can use a GPU in the attack, you must first select it in the respective item of the main menu.
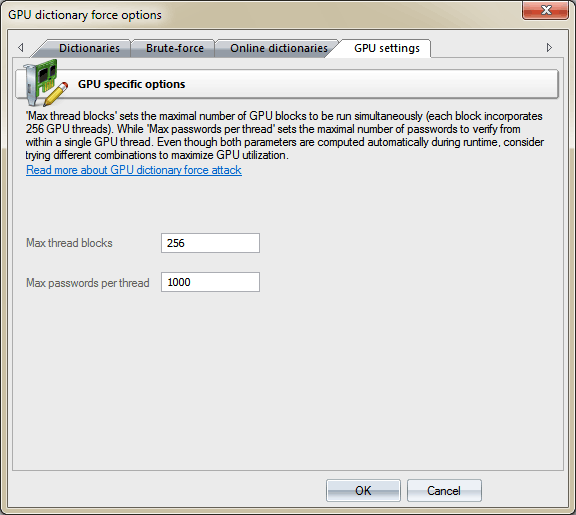
GPU configuration is pretty simple and consists of only two settings:
-
The number of parallel graphics card’s blocks, where passwords would be searched. Typically, each block consists of 256 threads. Thus, if you set the number of blocks to 256, the GPU will run 256*256=65536 threads. The total number of checked passwords for one call to GPU kernel will be 256*ThreadBlocks*PasswordsPerThread. In our case 256*256*1000 = 65 536 000 passwords. Setting the ThreadBlocks smaller than 256 on modern graphics cards, in the majority of cases, leads to performance degradation.
-
The number of passwords to be sought from a single thread. The greater the value, the lower the overhead associated with launching threads, and the higher the search speed. However, setting too great a value may hang the computer or cause significant fluctuations in the current search speed, displayed on the attack status tab. This is caused by the fact that task completion time on the GPU exceeds the time required for refreshing the current state of the attack.
Depending on the options you have specified, a proper choice of GPU settings can drastically, often by several times, increase the password search speed. Every time you change an option of the first two tabs, we recommend playing around with GPU settings to achieve the maximum utilization.




