Hash Encryption in Windows 10 Anniversary Update
 posted by Passcape_Admin at 11:59:40 06.12.2016
posted by Passcape_Admin at 11:59:40 06.12.2016Microsoft recently introduced a large anniversary update for Windows 10, one of its most popular operating systems.
Windows 10 Anniversary Update makes Windows 10 better than ever before. You can enjoy a multitude of new features, including:
- shuffle buttons in the Start menu
- take advantage of additional highly requested adware
- resize and reshape the adorable tiles
- admire how fast your personal data is sent to Microsoft
- try a brilliant monochrome skin for those suffering from moon blindness
- view brand new minimalistic icons developed by thousands of hard-working UI designers
- spend even more time searching for system options across multiple windows, thus raising the bar for your extrasensory perception
In all seriousness, however, the update does actually introduce some important improvements that deserve our attention. These include a Linux shell, pure re-installation, improved intelligence in Cortana, new login options based on Windows Hello, and much more.
The funny thing is that, despite the fact that the standard login workflow of Windows 10 has been slightly changed, this is not mentioned in the release notes at all. Due to these slight, yet significant changes, most hacker tools for pulling password hashes out of Windows will not work anymore. These changes may have been motivated by Microsoft's desire to discontinue support for legacy and vulnerable cryptographic algorithms. In our example, Microsoft has decided to discontinue support for RC4. Luckily, the latest version of Windows Password Recovery that is used for auditing Windows security has already got support for new SAM encryption scheme.
According to Microsoft, user passwords are stored as hashes (instead of plain-text representation) that can be accessed in the corresponding section of the Windows registry (only by the system itself):
HKLM/SAM/SAM/Domains/Account/users/<RID>/V.
Where <RID> - is the unique user ID.
Unique user IDs can be figured out by scanning the following registry tree:
HKLM/SAM/SAM/Domains/Account/users/names/<NAME>
Each key containing a username is associated with a corresponding RID. For example, the RID of the Administrator account is always equal to 500 (0x1F4 in the hexadecimal notation), while the Guest's RID is 501 (0x1F5).
Any user's registry key also holds at least 'C' and 'V' records. A 'V' record contains the variable-length data that corresponds to this account. The names themselves seem to be abbreviations – 'V' stands for 'variable' and 'C' means 'constant.' Each variable in the 'V' records is represented as a constant within the interval from 0 to 0xCC, e.g. a username is encoded as 0xC. Therefore, if we know the constant, we can identify an offset to the index that refers to actual data. LM and NT hashes correspond to 0x9C and 0xA8 respectively. However, obtaining the final password hash will require several additional decryption steps.
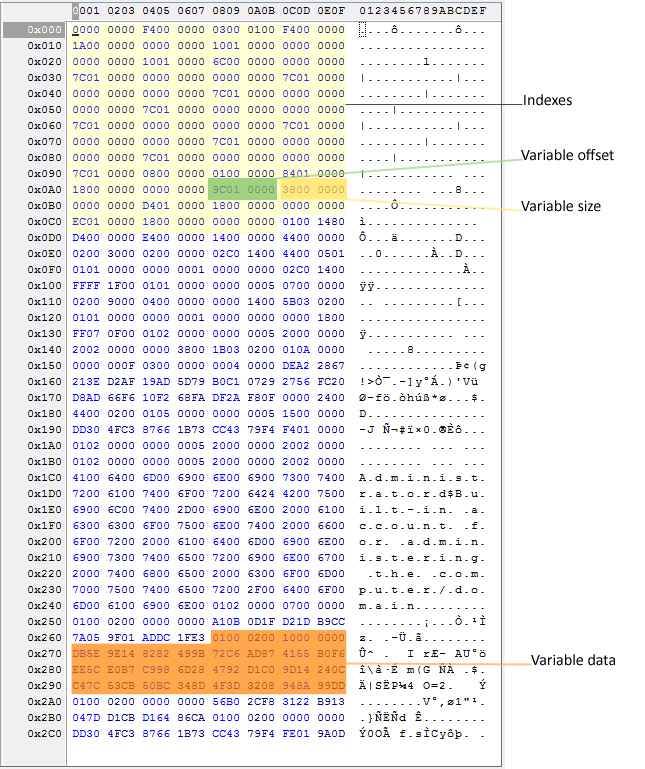
Let's see how the system generally retrieves the NTLM hash of a user:
- First of all, the system identifies a path to the key in the Windows registry where the account settings are stored, e.g. HKLM/SAM/SAM/Domains/Account/Users/00001F4
- The next step is to read the variable that contains the NTLM hash. This variable corresponds to the constant 0xA8. The system thus reads the data index based on the offset in this constant, i.e. 0x19C. Adding the data index to 0xCC will give the offset 0x268 from which we can access the actual data (our 'raw' NTLM hash) as shown in the picture. Now the system can read the hash and decrypt it.
- Using SYSKEY, the system decrypts the SAM session key. The SAM session key is stored in the registry section called HKLM/SAM/SAM/Domains/Account/V. This data structure actually keeps two encryption keys: the current one and the previous one. In this step, the system uses the MD5 and RC4 algorithms. In Windows 10 Anniversary Update, RC4 has been replaced with AES.
- The system then uses the SAM session key to decrypt the 'raw' hash obtained in Step 2 through the RC4 or AES (for Windows 10 Anniversary Update) algorithm.
- And, finally, the data that has been obtained is transformed once again into the actual data by means of the DES algorithm and the user's RID as the encryption key. Now our NTLM hash is ready.
As you can see, in Windows 10 Anniversary Update the RC4 stream cipher in Steps 3 and 4 has been replaced with the AES block cipher. This has led to certain changes in the data storage structure (at least because the data length in AES blocks must be multiple to 16 bytes) but has not resulted in stronger security of the operating system.












